Moving platform source
99
Web3privacynowplatform/Brief.md
Normal file
|
|
@ -0,0 +1,99 @@
|
|||
*Brief for a private web3-services*: please, follow general requirements to be highlighted on The Web3Privacy now platform.
|
||||
|
||||
How it works:
|
||||
1. You fill a brief.
|
||||
2. Our team reviews application.
|
||||
3. Verified data will be published at The Web3Privacy now platform.
|
||||
|
||||
# **Basic info**
|
||||
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Project name** | add here |
|
||||
| **Logotype** | add here |
|
||||
| **Short project description (1 sentence)** | add here |
|
||||
| **Launch date** | add here |
|
||||
| **Is it open source?** | specify here |
|
||||
| **Website** | add here |
|
||||
| **Github** | add here |
|
||||
|
||||
# **Optional info**
|
||||
|
||||
**Token**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Do you have a token** | add here Coingecko link |
|
||||
|
||||
**Socials**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Blog** | add link |
|
||||
| **Twitter (X)** | add link |
|
||||
| **Telegram** | add link |
|
||||
| **Discord** | add link |
|
||||
| **Other** | add link |
|
||||
|
||||
**Docs**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Docs** | add link |
|
||||
| **Whitepaper** | add link |
|
||||
| **Litepaper** | add link |
|
||||
|
||||
**Team**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Is your team anon or public** | choose one: anon, public |
|
||||
| **List core contributors** | Github links |
|
||||
|
||||
**Funding**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **How are you funded** | self-funded, VC, donations, mixed |
|
||||
| **List VCs backing you** | if aplicable |
|
||||
| **List VCs round** | if aplicable: pre-seed, seed, Series A, B,C |
|
||||
| **Raised money** | add a public link |
|
||||
|
||||
**Github**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **What licence is in use** | add link to Github repo |
|
||||
|
||||
**Technology**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Technical specialisation** | specify: ZK, account abstraction, mixnet etc |
|
||||
| **Specify technology readiness** | infra: testnet/mainnet, apps: MVP/beta/alpha |
|
||||
| **Features** | list 3 key tech features |
|
||||
| **Encryption method** | if aplicable: specify |
|
||||
|
||||
**Privacy**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Is it peer-to-peer** | yes/no |
|
||||
| **Complience** | yes/no |
|
||||
| **KYC** | yes/no |
|
||||
| **Privacy policy** | add link |
|
||||
| **Collected data** | specify what data do you collect |
|
||||
| **Data sharing** | specify what data you share with third-parties |
|
||||
| **Sign-in requirments** | specify what data is needed to start using service |
|
||||
| **Identity integrations** | do you use third-party identity services (like ENS, Gitcoin Passport etc) |
|
||||
|
||||
**Security**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Asset custody** | specify |
|
||||
| **Upgradability** | specify |
|
||||
| **Social dependency** | team, CEO |
|
||||
| **Third-parties dependency** | specify |
|
||||
| **Technical dependency** | specify: Ethereum, ZK etc |
|
||||
| **Have you been audited by a third-party** | yes/no |
|
||||
| **What company audited** | specify (one &/or many) |
|
||||
| **When you were audited** | date: D/M/Y (one &/or many) |
|
||||
| **Add links to the audits** | here |
|
||||
|
||||
**Roadmap (technical)**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **When product had been launched** | specify test-net (infra), MVP (dApp): date D/M/Y |
|
||||
| **When mainnet, beta had been launched** | specify main-net (infra), alpha (dApp): date D/M/Y |
|
||||
106
Web3privacynowplatform/Briefs/Brief 2.0.md
Normal file
|
|
@ -0,0 +1,106 @@
|
|||
*Brief for a private web3-services*: please, follow general requirements to be highlighted on The Web3Privacy now platform.
|
||||
|
||||
How it works:
|
||||
1. You fill a brief (at least "mandatory field").
|
||||
2. Our team reviews application.
|
||||
3. Verified data will be published at The Web3Privacy now platform.
|
||||
|
||||
# Mandatory data
|
||||
|
||||
## Basic info
|
||||
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Project name** | add here |
|
||||
| **Logotype** | add link |
|
||||
| **Website** | add link |
|
||||
| **Short project description (1 sentence)** | add here |
|
||||
| **Blog** | add link |
|
||||
| **Twitter (X)** | add link |
|
||||
| **Support** | add links on Discord, Telegram etc |
|
||||
|
||||
## Assessment info
|
||||
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Product-readiness** | specify state & date (testnet, mainnet; date D/M/Y) |
|
||||
| **Github** | add link |
|
||||
| **Documentation** | add link |
|
||||
| **Team** | add link to a team page (website or GitHub) |
|
||||
| **Third-party audit** | add links on actual audits + date D/M/Y |
|
||||
|
||||
# Additional data (non-mandatory)
|
||||
|
||||
**Token**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Do you have a token** | add here Coingecko link |
|
||||
|
||||
**Socials**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Telegram** | add link |
|
||||
| **Discord** | add link |
|
||||
| **Other** | add link |
|
||||
|
||||
**Docs**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Whitepaper** | add link |
|
||||
| **Litepaper** | add link |
|
||||
|
||||
**Team**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **List core contributors** | Github links |
|
||||
|
||||
**Funding**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **How are you funded** | self-funded, VC, donations, mixed |
|
||||
| **List VCs backing you** | if aplicable |
|
||||
| **List VCs round** | if aplicable: pre-seed, seed, Series A, B,C |
|
||||
| **Raised money** | add a public link |
|
||||
|
||||
**Github**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **What licence is in use** | add link to Github repo or a Docs page |
|
||||
|
||||
**Technology**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Technical specialisation** | specify: ZK, account abstraction, mixnet etc |
|
||||
| **Specify technology readiness** | infra: testnet/mainnet, apps: MVP/beta/alpha |
|
||||
| **Features** | list 3 key tech features |
|
||||
| **Encryption method** | if aplicable: specify |
|
||||
|
||||
**Privacy**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Is it peer-to-peer** | yes/no |
|
||||
| **Complience** | yes/no |
|
||||
| **KYC** | yes/no |
|
||||
| **Privacy policy** | add link |
|
||||
| **Collected data** | specify what data do you collect |
|
||||
| **Data sharing** | specify what data you share with third-parties |
|
||||
| **Sign-in requirments** | specify what data is needed to start using service |
|
||||
| **Identity integrations** | do you use third-party identity services (like ENS, Gitcoin Passport etc) |
|
||||
|
||||
**Security**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Asset custody** | specify |
|
||||
| **Upgradability** | specify |
|
||||
| **Social dependency** | team, CEO |
|
||||
| **Third-parties dependency** | specify |
|
||||
| **Technical dependency** | specify: Ethereum, ZK etc |
|
||||
| **Have you been audited by a third-party** | yes/no |
|
||||
| **What company audited** | specify (one &/or many) |
|
||||
| **When you were audited** | date: D/M/Y (one &/or many) |
|
||||
| **Add links to the audits** | here |
|
||||
|
||||
**Roadmap (technical)**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Add types & dates of product-maturity** | specify testnet (infra), MVP (dApp): date D/M/Y; mainnet, beta |
|
||||
97
Web3privacynowplatform/Briefs/Fileverse.md
Normal file
|
|
@ -0,0 +1,97 @@
|
|||
*Brief for a private web3-services*: please, follow general requirements to be highlighted on The Web3Privacy now platform.
|
||||
|
||||
How it works:
|
||||
1. You fill a brief.
|
||||
2. Our team reviews application.
|
||||
3. Verified data will be published at The Web3Privacy now platform.
|
||||
|
||||
**Basic info**
|
||||
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Project name** | add here |
|
||||
| **Logotype** | add here |
|
||||
| **Short project description (1 sentence)** | add here |
|
||||
| **Launch date** | add here |
|
||||
| **Is it open source?** | specify here |
|
||||
| **Website** | add here |
|
||||
| **Github** | add here |
|
||||
|
||||
**Token**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Do you have a token** | add here Coingecko link |
|
||||
|
||||
**Socials**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Blog** | add link |
|
||||
| **Twitter (X)** | add link |
|
||||
| **Telegram** | add link |
|
||||
| **Discord** | add link |
|
||||
| **Other** | add link |
|
||||
|
||||
**Docs**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Docs** | add link |
|
||||
| **Whitepaper** | add link |
|
||||
| **Litepaper** | add link |
|
||||
|
||||
**Team**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Is your team anon or public** | choose one: anon, public |
|
||||
| **List core contributors** | Github links |
|
||||
|
||||
**Funding**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **How are you funded** | self-funded, VC, donations, mixed |
|
||||
| **List VCs backing you** | if aplicable |
|
||||
| **List VCs round** | if aplicable: pre-seed, seed, Series A, B,C |
|
||||
| **Raised money** | add a Crunchbase link |
|
||||
|
||||
**Github**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **What licence is in use** | add link to Github repo |
|
||||
|
||||
**Technology**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Technical specialisation** | specify: ZK, account abstraction, mixnet etc |
|
||||
| **Specify technology readiness** | infra: testnet/mainnet, apps: MVP/beta/alpha |
|
||||
| **Features** | list 3 key tech features |
|
||||
| **Encryption method** | if aplicable: specify |
|
||||
|
||||
**Privacy**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Is it peer-to-peer** | yes/no |
|
||||
| **Complience** | yes/no |
|
||||
| **KYC** | yes/no |
|
||||
| **Privacy policy** | add link |
|
||||
| **Collected data** | specify what data do you collect |
|
||||
| **Data sharing** | specify what data you share with third-parties |
|
||||
| **Sign-in requirments** | specify what data is needed to start using service |
|
||||
| **Identity integrations** | do you use third-party identity services (like ENS, Gitcoin Passport etc) |
|
||||
|
||||
**Security**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **Asset custody** | specify |
|
||||
| **Upgradability** | specify |
|
||||
| **Social dependency** | team, CEO |
|
||||
| **Third-parties dependency** | specify |
|
||||
| **Technical dependency** | specify: Ethereum, ZK etc |
|
||||
| **Have you been audited by a third-party** | yes/no |
|
||||
| **What company audited** | specify (one &/or many) |
|
||||
| **When you were audited** | date: D/M/Y (one &/or many) |
|
||||
| **Add links to the audits** | here |
|
||||
|
||||
**Roadmap (technical)**
|
||||
| Request | Data point |
|
||||
| ------------- | ------------- |
|
||||
| **When product had been launched** | specify test-net (infra), MVP (dApp): date D/M/Y |
|
||||
| **When mainnet, beta had been launched** | specify main-net (infra), alpha (dApp): date D/M/Y |
|
||||
1
Web3privacynowplatform/Briefs/Readme.md
Normal file
|
|
@ -0,0 +1 @@
|
|||
Here we test: the Web3Privacy now company reporting
|
||||
78
Web3privacynowplatform/Builder log.md
Normal file
|
|
@ -0,0 +1,78 @@
|
|||

|
||||

|
||||
|
||||
**8 march, spaceship Earth**
|
||||
- Created a table with 50+ privacy-services recommendations from Sismo to Privacy&Scalability explorations for non-techies assesment [Link](https://docs.google.com/spreadsheets/d/1JWpAsGL10UTsVeuIVbouzUxRjaSPUAamxcbFljXuUWE/edit?usp=sharing)
|
||||
- Created a concept that assumes that not every techie could "read&understand" the tech side like code equally (junior dev vs CTO) [Link](https://docs.google.com/spreadsheets/d/1JWpAsGL10UTsVeuIVbouzUxRjaSPUAamxcbFljXuUWE/edit?usp=sharing). At the moment categories are: docs, code, transaction tracibility. Potential categories: cross-chain assesment, cross-services assesment (Layer-1 vs Mixers).
|
||||
|
||||
The next big thing: have an assesment by the tech side of the privacy teams.
|
||||
|
||||
**16, feb, spaceship Earth**
|
||||
Had a call with Ethereum Foundation. They would love to understand if non-biased/objective scoring model is possible & at which stage.
|
||||
This is a challenging issue because if players didn't make one within years of privacy services existence & their general competitive attitude - this could take ages to accomplish.
|
||||
|
||||
- [Fileverse](https://twitter.com/miroyato/status/1626222748707225602)
|
||||
|
||||
**15 feb, spaceship Earth**
|
||||
|
||||
Continue to collect privacy-services tips how non-techies could be ensured that they use private tech
|
||||
- [Lava](https://twitter.com/lavanetxyz/status/1625781267110264832)
|
||||
- [Holonym](https://twitter.com/NanakNihal/status/1625655312832135168)
|
||||
- [Spinner Cash](https://twitter.com/spnrapp/status/1625666410612506625)
|
||||
- [Session](https://twitter.com/session_app/status/1625712450875326465)
|
||||
- [ZKBob](https://twitter.com/koal_/status/1625752877095436288)
|
||||
- [Litentry](https://twitter.com/KariSays_wen/status/1625861241536413696)
|
||||
- [BrightID](https://twitter.com/bitsikka/status/1625853432925130753)
|
||||
- [Swarm](https://twitter.com/ethswarm/status/1625836528499818497)
|
||||
- [Railgun](https://twitter.com/tsu_kareta/status/1625864200504442882)
|
||||
- [Penumbra](https://discord.com/channels/824484045370818580/824484046335246348/1075421328317874176)
|
||||
|
||||
**13-14 feb, spaceship Earth**
|
||||
I decided to ask private projects & their core team publicly how to measure whenever their solutions are private. Important note: it should work for non-techies.
|
||||
|
||||
Opinions are great for future scoring building:
|
||||
|
||||
- [SCBuergel.eth from HOPR](https://twitter.com/SCBuergel/status/1625424568314654723)
|
||||
- [Privacy & Scaling explorations](https://discord.com/channels/943612659163602974/956556086767403038/1075178542465306644)
|
||||
- [Waku](https://twitter.com/waku_org/status/1625276654624075778)
|
||||
- [Lefteris Karapetsas](https://twitter.com/LefterisJP/status/1625269056365363200)
|
||||
- [webb](https://twitter.com/webbprotocol/status/1625332620942008320)
|
||||
- [Boring Protocol](https://twitter.com/BoringProtocol/status/1625322766462500864)
|
||||
- [Lit protocol](https://twitter.com/LitProtocol/status/1625322308821811203)
|
||||
- [Alter community](https://twitter.com/AnewbiZ007/status/1625278499606106112)
|
||||
- [Sons of crypto](https://twitter.com/web3d3v/status/1625476576811839496)
|
||||
- [Orbis community](https://twitter.com/BaptisteGreve/status/1625475768946946049)
|
||||
- [Nighthawk Wallet](https://twitter.com/aiyadt/status/1625484422936989697)
|
||||
- [KILT protocol](https://twitter.com/ingoruebe/status/1625500194816266240)
|
||||
- [Onion club](https://twitter.com/onionclub_io/status/1625501848189939719)
|
||||
- [Sismo](https://twitter.com/dhadrien_/status/1625488518696022019)
|
||||
- [Krebit](https://twitter.com/KrebitID/status/1625508542391234565)
|
||||
- [Puma browser](https://twitter.com/PumaBrowser/status/1625506944613249029)
|
||||
- [hideyourcash](https://twitter.com/hideyourcash/status/1625509914805239808)
|
||||
- [EdenBlockVC](https://twitter.com/cleanunicorn/status/1625513229152665600)
|
||||
- [Elusiv](https://twitter.com/elusivprivacy/status/1625517643481374721)
|
||||
- [Beam](https://twitter.com/maxnflaxl/status/1625518069769543683)
|
||||
- [Railgun](https://twitter.com/therealjmj/status/1625581000829853734)
|
||||
- [Findora](https://twitter.com/PaganD/status/1625618088640274432)
|
||||
- [Leo wallet](https://twitter.com/theLeoWallet/status/1625620029076291585)
|
||||
- [Scala](https://twitter.com/ScalaHQ/status/1625554059821256714)
|
||||
- [Media Foundation](https://twitter.com/Media_FDN/status/1625558638608715800)
|
||||
- [Aleo community](https://discord.com/channels/700454073459015690/700465638937722951/1075174751510732870)
|
||||
- [Automata community](https://discord.com/channels/812990347114315786/812990347114315789/1075175812875161611)
|
||||
|
||||
**10 feb, spaceship Earth**
|
||||
|
||||
Had a call with Nick Havrilyak (experienced product manager). We discussed different approaches to scoring modelling, on-chain & off-chain data management, indexing protocols etc.
|
||||
|
||||
**Few observations**
|
||||
- lots of privacy scoring directions are highly subjective (like "if a team is ideological") & can't be automated in the DB
|
||||
- The scoring model MVP would be oversimplified.
|
||||
- Because the ultimate goal -> on-chain reputation x privacy services (where Unirep Protocol & co are headed)
|
||||
- But there should be a point on a roadmap to receive non-expert opinions from the people who would use privacy services. I think there will be interesting insights into how they would approach assessment & "trust" (especially within non-web3 people).
|
||||
|
||||
**To do**
|
||||
- apply a "subjective/objective" lens to Expert recommendations
|
||||
- use "on-chain/off-chain" lens to recommendations
|
||||
- analyze "objective" cohort
|
||||
- analyze "on-chain" cohort
|
||||
- create a simplified MVP vision (easy to deliver & scale further to more complex model)
|
||||
139
Web3privacynowplatform/Readme.md
Normal file
|
|
@ -0,0 +1,139 @@
|
|||
_visual prototype_
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/Visual%20prototype.png" width="700"/>
|
||||
|
||||
# Progress
|
||||
|
||||
1. **Scoring progress** [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Readme.md)
|
||||
2. **UI progress** [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/UI/Readme.md)
|
||||
|
||||
# Project description
|
||||
[](https://twitter.com/intent/follow?screen_name=nicksvyaznoy)
|
||||

|
||||
|
||||

|
||||
|
||||
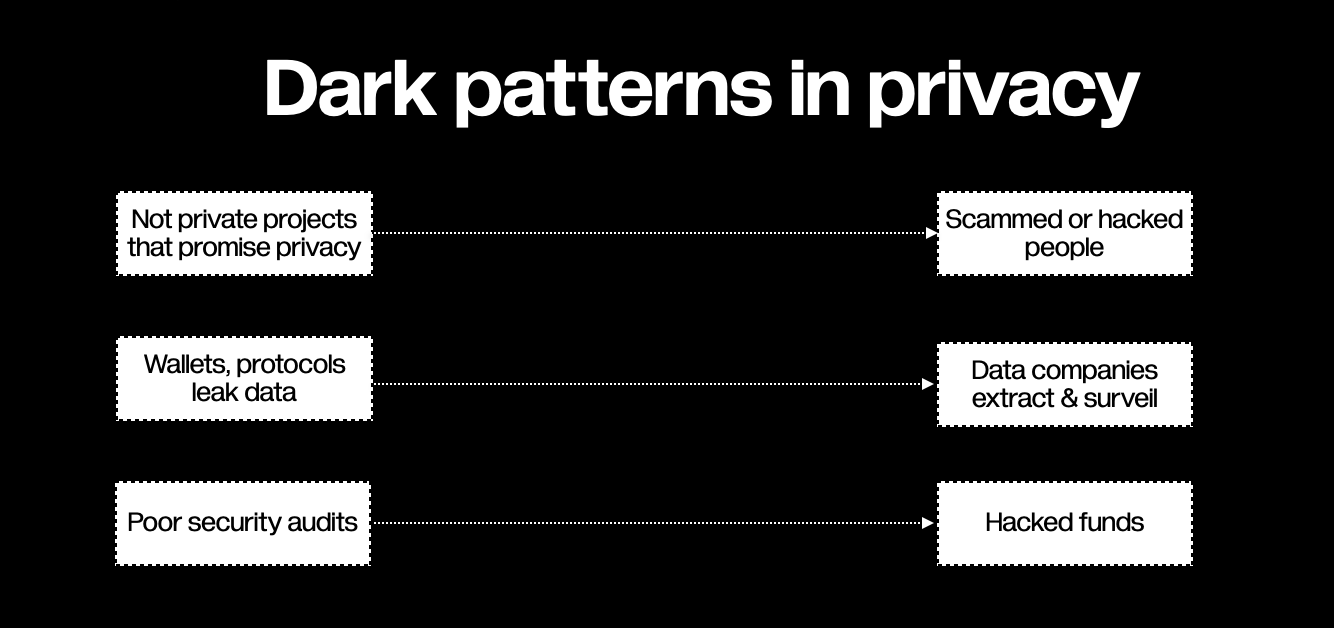
Privacy is a top priority in the era of web, an essential human right. Web3privacy now would create a scoring mechanism (both professional & communal) to provide unbiased tools for assessing projects & helping users through education, raising our collective privacy literacy.
|
||||
|
||||
|
||||
|
||||

|
||||
|
||||
|
||||
|
||||
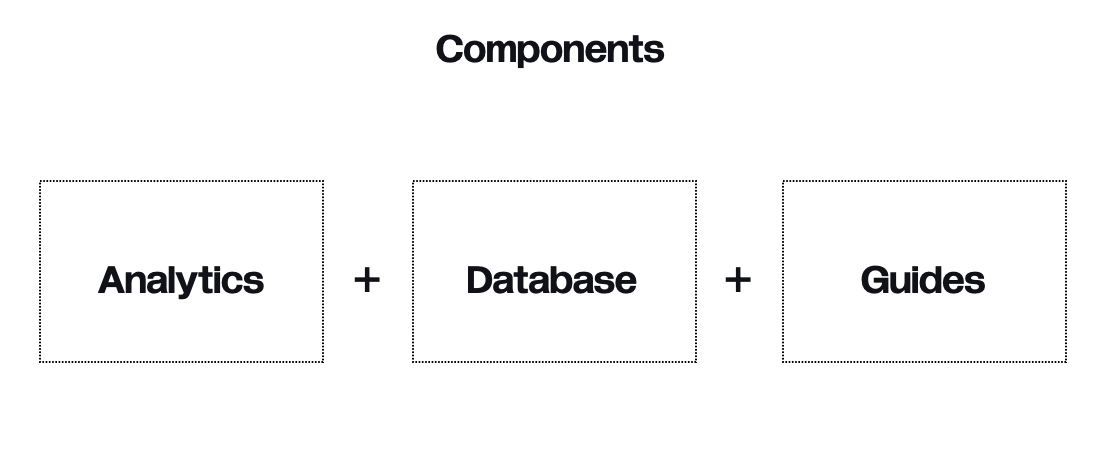
# Platform features
|
||||
|
||||
|
||||
- **Scoring mechanism**
|
||||
We'll reserach and develop a unique privacy scoring mechanism & create a tool with the help of privacy experts from the Ethereum Foundation, NYM and others while building on the experiene of active members from both solar and lunarpunk communities. The goal is to collectively raise the maturity of privacy products & services accross all layers of the technology stack.
|
||||
|
||||
In parallel to the top-down scorecard method, we'll develop and implement a bottom-up community scoring platform too (think of Metacritic exters + users scorings). We believe that at the end of the day it's the users who have to become the real watchdogs of the industry, signaling about flaws and shortcomings of solutions (like Secret Network's recent critical bug).
|
||||
|
||||
Critical approach: professional scoring would be a joint R&D with the key web3 people from protocol architects to security specialists. This will help to create an unbiased take from scratch & enabling a transparent working process, accessible to everyone via a forum.
|
||||
|
||||
_References_: www.l2beat.com + www.certik.com + https://www.metacritic.com/about-metascores + [Clutch](https://clutch.co/methodology)
|
||||
|
||||
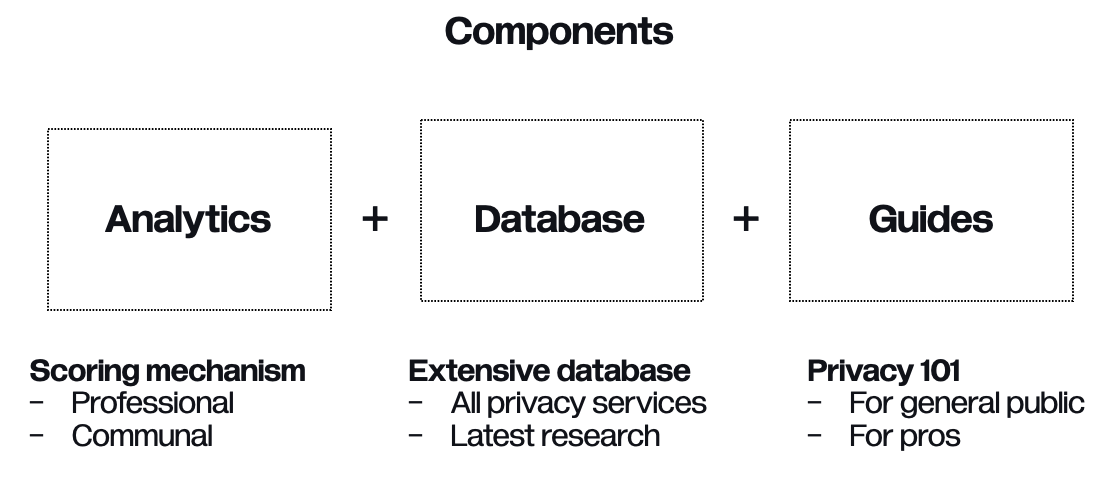
|
||||
|
||||
- **Privacy services database**
|
||||
The biggest privacy services database with the latest R&D tracks from [Privacy & Scaling explorations](http://appliedzkp.org) to [Chainsafe](http://chainsafe.io) proposals.
|
||||
Highly helpful to everyone exploring & researching cutting-edge of the privacy stack (including builders & hackathon-enablers).
|
||||
|
||||
Access it here: https://github.com/Msiusko/web3privacy
|
||||
|
||||
**Privacy guides**.
|
||||
Extensive privacy guides covering broad audiences from Iranian human rights activists to Ukrainian people living on occupied territories.
|
||||
|
||||
_Practical guides will match_
|
||||
|
||||
- existing privacy solutions from Sismo to NYM with privacy-personas (NGOs, anon donors, activists).
|
||||
- non-tech people with accessible privacy solutions (with the focus on human rights & sensitive audiences)
|
||||
- tech-people with advanced privacy solutions & practices
|
||||
|
||||
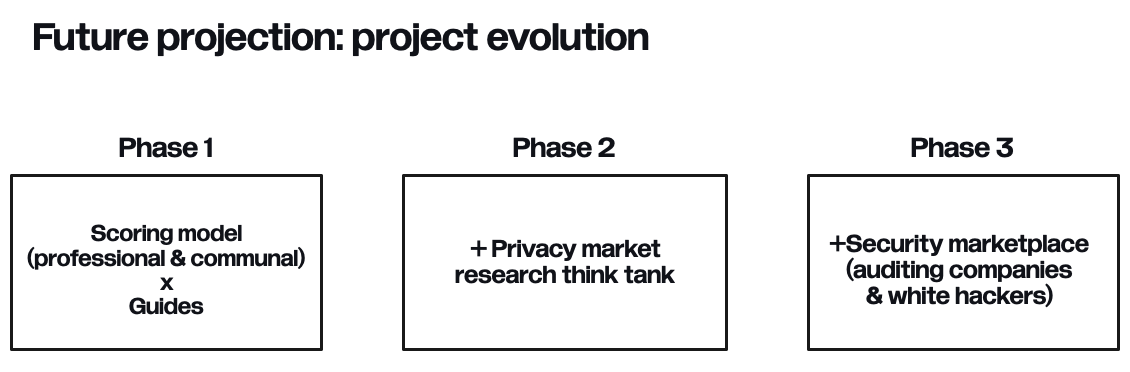
# How the future looks for Web3privacy now
|
||||
|
||||
|
||||
- **Privacy hub**. Becoming the leading online privacy repository, empowering anyone with access the latest insights, analysis and data from across the industry.
|
||||
- **Privacy education**. Extensive wiki about privacy technology and user-focused service literacy. Guides created by community experts, evaluated by users.
|
||||
- **Privacy advocacy**. We don't only promote privacy, but more broadly: we'll be working on normalising the concept of privacy as an inalienable human right. We'll catalyse the shift of the meta-narrative and perception within the entire society: investors, decision makers, developers, web3 & web2 actors and the general public too.
|
||||
|
||||
# So what's next
|
||||
1. Grant: for the initial project research & MVP delivery (scoring mechanism principles, MPV scope, team structures, basic project management tools subs).
|
||||
2. Dev scope: stack + scope of work + dev team
|
||||
3. MVP: definition + timing + KPIs
|
||||
4. GitHub transparency: all repos, all roadmaps, public team members, scoring principles etc.
|
||||
|
||||
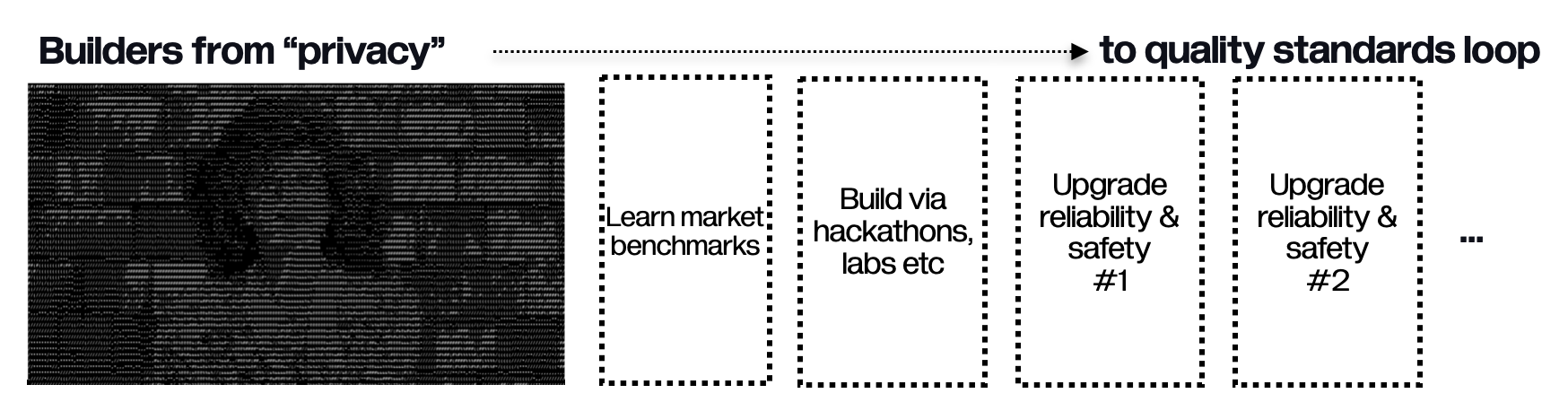
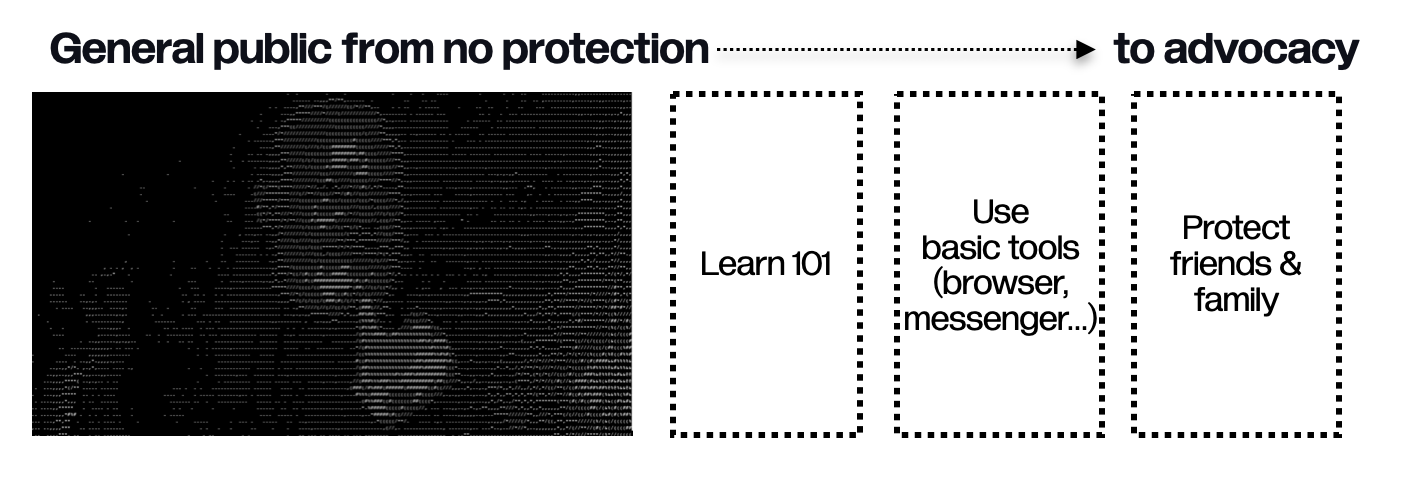
# Audiences
|
||||
|
||||
|
||||
|
||||
# KPIs
|
||||
**MVP-centric**
|
||||
- **Research track**: scoring model v 1.0 + expert validation
|
||||
- **Product track**: basic functionality mapping (incl. UX/UI research), copywriting, basic brand design system, scoring model applicability to all existing privacy-preserving web3 projects (300+ projects).
|
||||
- **Tech delivery track**: v 1.0 website (minimum functionality for testing), QA, bug fixing
|
||||
- **Community accessibility & awareness**: socials registration, community development, forum setup.
|
||||
|
||||
**Note**: _governance model - in consideration_
|
||||
|
||||
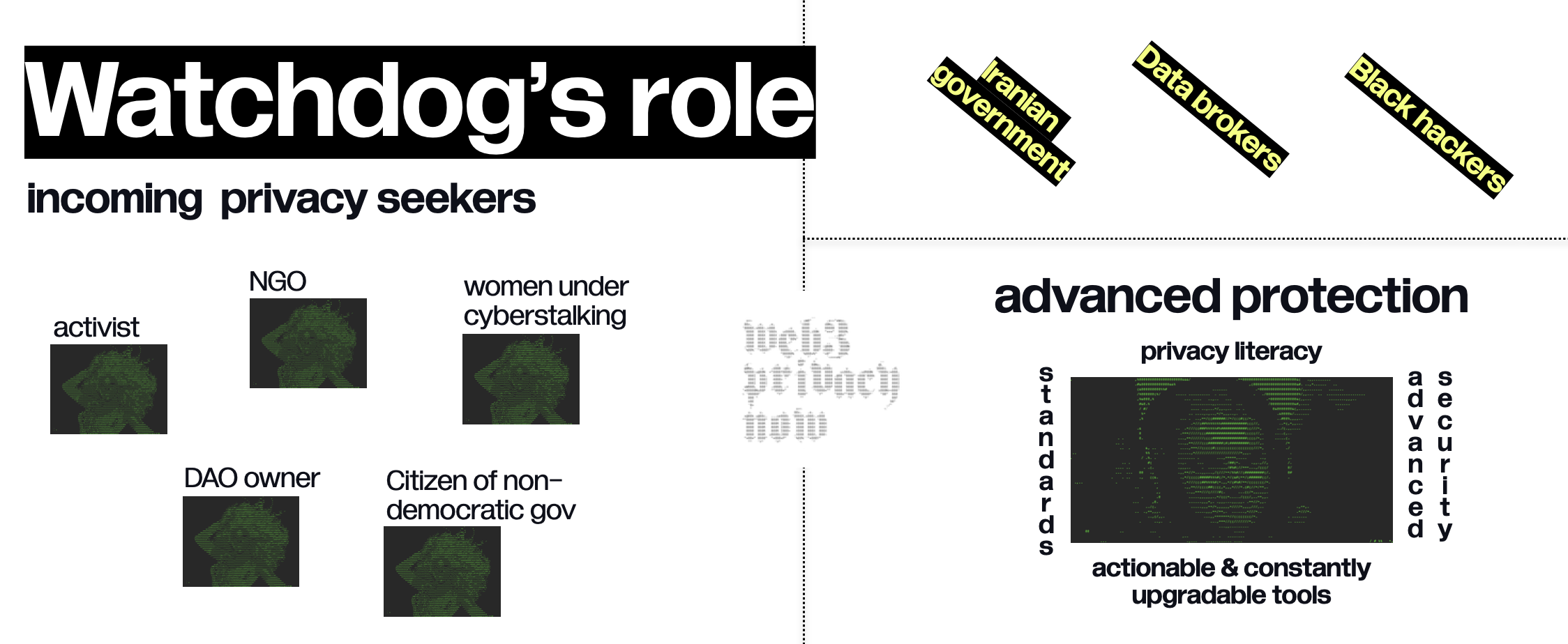
**Beta**
|
||||
The next product release will include
|
||||
- **community feddback **(voting for the projects, writing user-feedback etc)
|
||||
- **leaderboard** (categories) to motivate companies compete with each other for better privacy preservation.
|
||||
- **incidents dabatse**: [Press Freedom Tracker](https://pressfreedomtracker.us/all-incidents/) example
|
||||
|
||||
|
||||
|
||||
# Timing
|
||||
**Time-to-MVP > 3 months**
|
||||
|
||||
**Breakdown**:
|
||||
- **Scoring modeling**: 3 weeks+
|
||||
- **Product management** (UX, copy, scoring aplicability, design): 1 month
|
||||
- **Web-development + testing**: 1 month
|
||||
|
||||
**In a nutshell**:
|
||||
- a research paper: scoring model > sketch is available [here](https://github.com/Msiusko/web3privacy/blob/main/Web3privacynowplatform/Scoringmodel.md)
|
||||
- a code repo at GitHub
|
||||
- working website + public scoring model.
|
||||
|
||||
# Team
|
||||
**MVP-centric**
|
||||
|
||||
|
||||
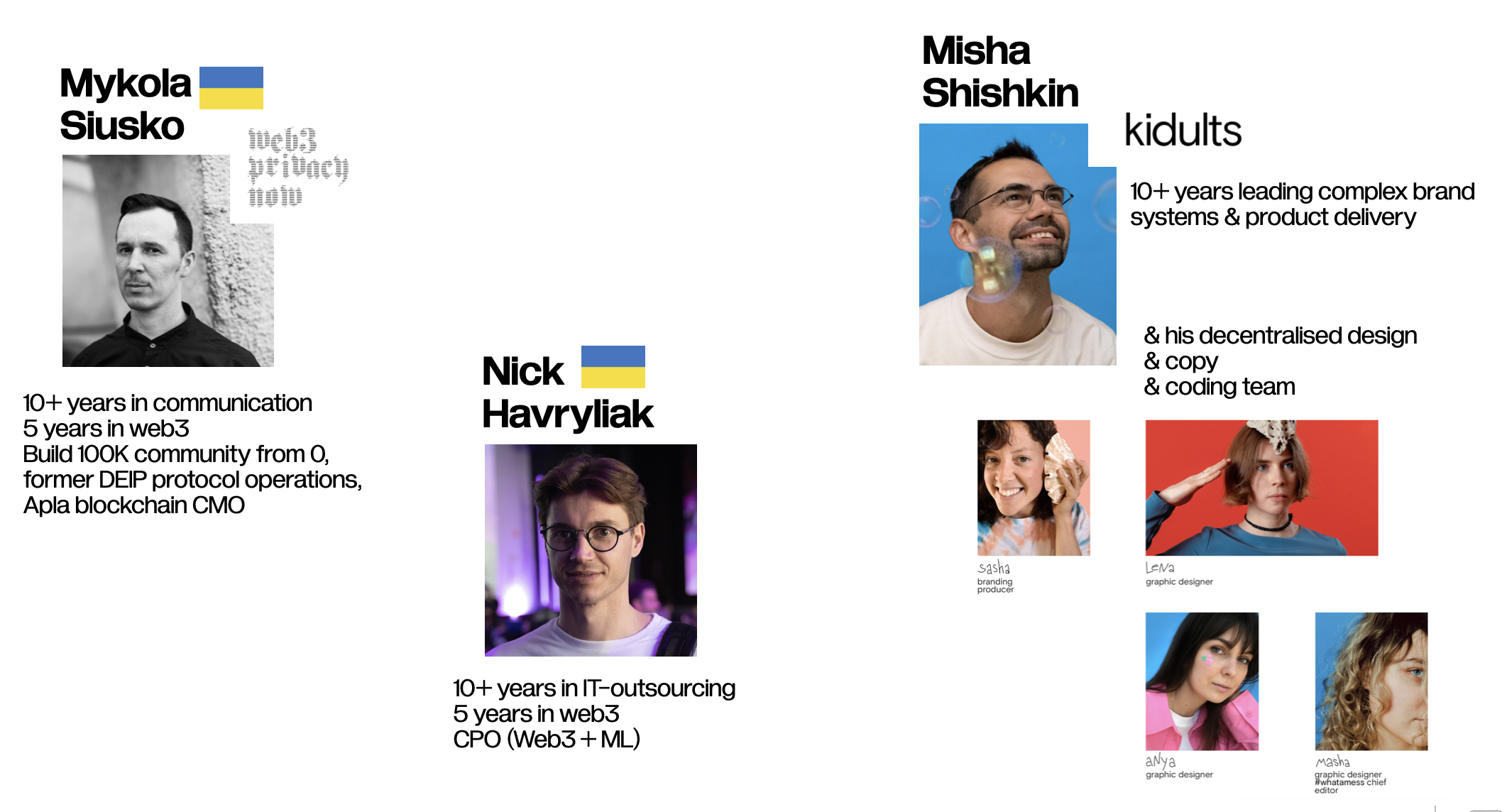
- **MVP-management**: core project manager > Mykola Siusko [GitHub](http://github.com/Msiusko), [Twitter](http://twitter.com/nicksvyaznoy), [LinkedIn](http://linkedin.com/in/siusko/)
|
||||
- **Research track**: Mykola Siusko, Pineapple Proxy (https://pnproxy.org)
|
||||
- **Product**: [Nick Havryliak](https://www.linkedin.com/in/havryliak/)
|
||||
- **Design & coding track**: [Misha Shishkin](https://www.linkedin.com/in/mikeshishkin/) lead decentralised design agency [Kidults](https://wearekidults.com) - female-led UX/UI, 1x copywriter, 1x designer, 1x project manager
|
||||
- **Community accessibility & awareness**: Pineapple Proxy
|
||||
|
||||
_Total_: 7 FTE + advisor community
|
||||
|
||||
|
||||
# Where we are now
|
||||
0. Homework has been done: 350+ projects in the public [database](https://github.com/Msiusko/web3privacy), ZK projects [database](https://github.com/Msiusko/web3privacy/tree/main/ZKprivacylandscape), Market research [outlook](https://github.com/Msiusko/web3privacy/blob/main/Market%20overview/Privacy%20market%20outlook%20in%20Web3%20by%20Mykola%20Siusko%20(Jan%202023).pdf)
|
||||
1. Searching for grants: [contact](http://twitter.com/nicksvyaznoy)
|
||||
2. BUIDLing with the extended team.
|
||||
|
||||
|
||||
|
||||
# Value for ecosystem (donors)
|
||||
|
||||
**PR**
|
||||
- Strong contribution to the general security level of the new web
|
||||
- Positive industry image (counter-crime & scam argument)
|
||||
- Non-web3 literate but privacy conscious user education and onboarding (increasing accessibilty and real-world use cases of decentralised technologies)
|
||||
|
||||
**Scoring mechanism**: aplicability to ecosystem's projects
|
||||
|
||||
**Builders empowerment**: builder-ready educational materials & tools
|
||||
|
||||
# Donate
|
||||
|
||||
Support independent research on the Web3 privacy
|
||||
- **BTC**: 3Fk68ZcG9dFyXecr8qW1JM1195JHpUkD2A
|
||||
- **ETH**: 0x2465193c113E524C704413b7af6A5517bF5d2BEE
|
||||
- **USDT** (TRC20): TD6DexUT71M24cUouCV22A1iKMWZmS4BU4
|
||||
- **ZEC**: t1JXUewb165Jfxv8bFAvsDHWbTpoAAeqCY1
|
||||
|
||||
#freealex
|
||||
267
Web3privacynowplatform/Scoringmodel.md
Normal file
|
|
@ -0,0 +1,267 @@
|
|||
# Privacy scoring modelling > Web3privacy now analytical [platform](https://github.com/Msiusko/web3privacy/tree/main/Web3privacynowplatform)
|
||||
|
||||
**Approach**
|
||||
|
||||
| Phase | Description |
|
||||
| ------------- | ------------- |
|
||||
| 1. **Expert take** | Outreach privacy experts behind core privacy services - aggregate their professional opinions on how to analyze if a service is truly private or not.) |
|
||||
| 2. **Scoring model prototyping** | Create an open & flexible scoring model for a communal feedback loop - share with the privacy community, evaluate. |
|
||||
| 3. **Scoring model MVP release** | Deliver balanced model for privacy services assessment - powered by pros & general public opinions. |
|
||||
|
||||
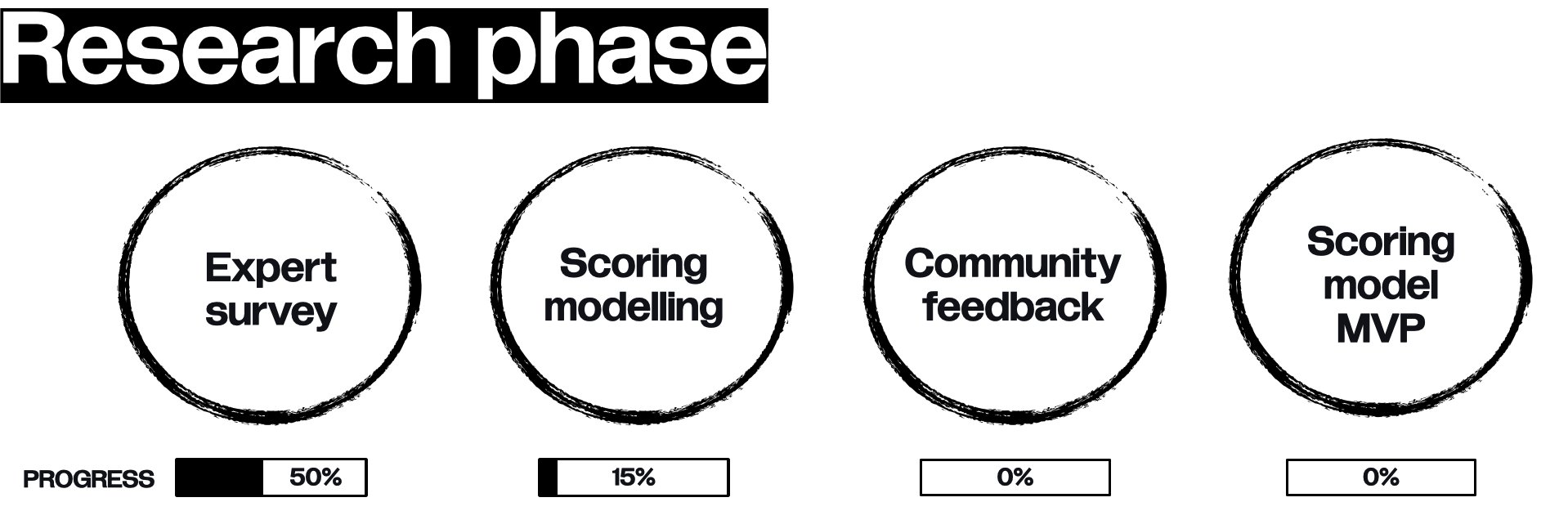
# Current status (02/04/2023)
|
||||
|
||||
|
||||
|
||||
## 0. 350+ privacy solutions in 1 database - [delivered](https://github.com/Msiusko/web3privacy/blob/main/README.md)
|
||||
## 1. On-going community research (survey) within the privacy experts.
|
||||
I asked experts behind privacy-services or contributors to the privacy-centric communities to share their visions on analysing whether a service is private. Answers were collected via chats & survey [form](https://forms.gle/ETBEZed9LUUtLWT87)
|
||||
|
||||
**Criteria**:
|
||||
- min 50 different experts
|
||||
- a broad range of positions: tech, ops, marketing, devrel, strategy
|
||||
- a broad range of services: from privacy coins to mixnets
|
||||
- different geographies: from the USA to Russia
|
||||
|
||||
# Questions from the privacy experts
|
||||
|
||||
# Take 1
|
||||
- does it has traceability? (ie addresses is hidden from the public ledger)
|
||||
- does it has unlinkability? (ie transactions can't be linked to each other)
|
||||
- does the amount of transfer is hidden?
|
||||
- does IP addresses of participants hidden?
|
||||
- is it decentralized and based on open-source technology?
|
||||
|
||||
# Take 2
|
||||
|
||||
| Question | Observation |
|
||||
| ------------- | ------------- |
|
||||
| much the users in control of their data disclosure? | (Scale 1-10) |
|
||||
| how well community feedback and evaluation is built into product dev? | the less -» the more centralized it is -» the smaller the % of it staying private without collective intelligence. This is like the web3privacynow - platform part, actually, for sales, but also I found this really relevant. |
|
||||
| is there a community bug/security bounty program/platform? | yes, no |
|
||||
| how much transparent disclosure is available on the tech and company | like smart contract audits, security audits, source of financing? |
|
||||
| how private the tech stack it uses on all layers. from hardware to l3/l4 etc. | how well it is disclosed what they built on and where they host stuff, or if the tech is decentralized like nym - is there available dashboard data about this? |
|
||||
| product roadmap and release flexibility - this is a harder one, and I'm not sure it makes sense. What I mean is it's also important to have a clear vision while reacting to current needs/bugs /fixing vulnerabilities. | maybe its redundant with no2 and no2b |
|
||||
|
||||
# Take 3
|
||||
1. What are the trust assumptions the user has by using the platform?
|
||||
2. What and how is user information stored and transmitted?
|
||||
3. How much PII is stored/collected?
|
||||
4. How is information collected + processed + disseminated
|
||||
5. How completely can you participate with total privacy?
|
||||
|
||||
# Take 4
|
||||
|
||||
| Direction | Observation |
|
||||
| ------------- | ------------- |
|
||||
| network privacy | how do you connect to the chain? Can you do it via Tor? |
|
||||
| blockchain privacy | do the resulting on-chain transactions offer the user any on-chain obfuscation? |
|
||||
| censorship resistance | how resistant is the project to external pressure? Will the project censor you? |
|
||||
| permission | do I need to create an account to access the thing, or is the thing open access? |
|
||||
| custody of funds | is the user out of control of their keys at any point? |
|
||||
|
||||
# Answers from the privacy experts
|
||||
**Additional lenses**: _is it accessible to a non-web3 person & is it accessible to a non-tech web3 person?_
|
||||
|
||||
## Contents
|
||||
- [General](#General)
|
||||
- [Docs](#Docs)
|
||||
- [Third-party analysis](#Third-party-analysis)
|
||||
- [VCs](#VCs)
|
||||
- [Team](#Team)
|
||||
- [Privacy policy](#Privacy-policy)
|
||||
- [Token](#Token)
|
||||
- [Infrastructure](#Infrastructure)
|
||||
- [Storage](#Storage)
|
||||
- [Data aggregation](#Data-aggregation)
|
||||
- [Traction](#Traction)
|
||||
- [Governance](#Governance)
|
||||
- [Privacy execution](#Privacy-execution)
|
||||
- [Product-centric](#Product-centric)
|
||||
- [Testing](#Testing)
|
||||
- [Other](#Other)
|
||||
|
||||
# General
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Immutability | - | - |
|
||||
| Decentralised throughout, including hosting | - | - |
|
||||
| Permissionless & accessible to all | - | - |
|
||||
| Open-source | + | + |
|
||||
|
||||
# Docs
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| read the documentation | - | - |
|
||||
| Good and comprehensive documentation | - | - |
|
||||
|
||||
# Third-party analysis
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| ask about its weaknesses from competitors | + | + |
|
||||
| Number of peer-reviewed articles at conferences and journals of team members | + | + |
|
||||
| Where's the code? Has it been audited? | + | + |
|
||||
| Validation by trusted and respected independent scientists and researchers | + | + |
|
||||
|
||||
# VCs
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Who are the VCs | - | - |
|
||||
| Not funded by big US VCs like a16z | - | + |
|
||||
|
||||
# Team
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| ideological team | - | + |
|
||||
| Reputation of the team | - | + |
|
||||
| is it purely marketing oriented, or it seems created by researchers/developers, are the developers anons? | + | + |
|
||||
|
||||
# Privacy policy
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Privacy Policy content | + | + |
|
||||
| Non-vague and non-intrusive privacy policy | + | + |
|
||||
| #privacy protection policies | + | + |
|
||||
|
||||
# Token
|
||||
| Scoring | Non-web3 person assesment | Web3, but non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| is there a token since the beginning? | - | + |
|
||||
| if the token since beginning - weird | - | + |
|
||||
|
||||
# Infrastructure
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| How much to run a node | - | + |
|
||||
| Where are the nodes | - | + |
|
||||
| Number of nodes/servers/ -> the larger the footprint the best privacy | - | + |
|
||||
|
||||
# Storage
|
||||
| Scoring | Non-web3 person assesment | Web3, but non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| e2e encrypted LOCAL storage | - | + |
|
||||
| What user information is stored? (username, IP address, last connection, wallets associate, etc) | - | + |
|
||||
| Where is it stored? (centralized server, certain jurisdictions, on-chain, in browser/local cache) | - | + |
|
||||
|
||||
# Data aggregation
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| no email or tel nr for signup | + | + |
|
||||
| control over personal data | - | - |
|
||||
| does not implement KYC or AML | + | + |
|
||||
| Metadata privacy / Minimal to no metadata capture | - | - |
|
||||
|
||||
# Traction
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Amount of transactions | + | + |
|
||||
| number of people using it | + | + |
|
||||
| is it famous | + | + |
|
||||
| Latency | - | - |
|
||||
| Time of test and battle-tested code - (e.g. how BSC had passed the stress time of withdrawals with FTX drama or crypto schemes such as ECDSA with more than 2-3 decades alive) | - | - |
|
||||
| Cost | - | + |
|
||||
|
||||
# Governance
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| DAO structure (if applied) | - | + |
|
||||
|
||||
# Privacy execution
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| How is it being transmitted? (encrypted, unencrypted, offuscated, etc) | - | - |
|
||||
| Combined those encryption methods effectively (holistic solution) | - | - |
|
||||
| Confidentiality of transactions | - | - |
|
||||
| the ability to hide transactional data from the public | - | - |
|
||||
| strong encryption algorithms | - | - |
|
||||
| If the speed in connection is too fast, there most probably no privacy there and rather a direct channel between user - app | - | - |
|
||||
| p2p / no central server | - | - |
|
||||
| Trustless - No ID required (this is where ZKs are useful) | - | + |
|
||||
| Usage of ZK | - | - |
|
||||
|
||||
# Product-centric
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Onboarding steps | + | + |
|
||||
| Usability - for end users or in the developer experience if it is a B2B project. | + | - |
|
||||
|
||||
# Testing
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Ability to run part of the service and verify for myself | - | - |
|
||||
| try to trace a transaction | - | - |
|
||||
| There is a way to verify the code I think is running, really is running e.g. attestation service | - | - |
|
||||
| Other tooling to verify e.g. block explorers | - | + |
|
||||
|
||||
# Other
|
||||
| Scoring | Non-web3 person assesment | Non-tech assesment |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| Entropy (non-trivial to estimate, different measurements for type of service). Some examples: https://arxiv.org/abs/2211.04259 or https://blog.nymtech.net/an-empirical-study-of-privacy-scalability-and-latency-of-nym-mixnet-ff05320fb62d | - | - |
|
||||
| Censorship-resistant (how hard it's for a powerful party to block/censor a given service) | - | - |
|
||||
| Precise description of the concrete privacy properties. Privacy is complicated, so if they don't say exactly what they protect, then its likely vapour | - | - |
|
||||
| Doesn’t sell your data | - | - |
|
||||
| protects against a global passive adversary | - | - |
|
||||
| strong secure anonymity tech | - | - |
|
||||
| Credibly neutral | + | + |
|
||||
| ISO/IEC 29190:2015: https://www.iso.org/standard/45269.html | - | - |
|
||||
| Anonymity Assessment – A Universal Tool for Measuring Anonymity of Data Sets Under the GDPR with a Special Focus on Smart Robotics: https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3971139 | - | - |
|
||||
|
||||
_Huge thanks everyone who contributed! I make it anon now, but will thank everyone (who would liked to be credited) once a scoring model will be published on GitHub for community evaluation._
|
||||
|
||||
# 2. My personal notes on privacy scoring (they were made before communal survey)
|
||||
_Sketches what could be put inside privacy-solutions scoring model_ (note: think of these as questions to experts for a workshop on scoring ideation).
|
||||
|
||||
**Key observations**
|
||||
|
||||
| Topic | Observation |
|
||||
| ------------- | ------------- |
|
||||
| Broad range of different takes on privacy assesment | Privacy experts have around 50+ tips |
|
||||
| Tech-centricity of assesment | Majority of the expert takes are hard to execute by non-tech people (they need info-help!) |
|
||||
| Privacy assessment takes enormous time | Time-To privacy-fit - potential for analytical service |
|
||||
| Privacy literacy isn't enough | The scoring model demand both "decentralisation", "open-source" & "privacy" topics understanding |
|
||||
| Mix of objective & subjective takes | Scoring criteria are different from objective (example: transaction traceability) & subjective (example: backed by a16z crypto) takes |
|
||||
|
||||
**Open-source transparency**
|
||||
- **GitHub repos**: # of commits, # stars, date of repo creation.
|
||||
|
||||
**Third-party validation**
|
||||
- **Security audits**: yes, no; type of audit; ammount of audits.
|
||||
|
||||
**Community validation**
|
||||
- Existing bugs
|
||||
- White hackers assessment (like Secret Network TEE bug)
|
||||
- Negative Discord, Twitter, other public feedback (product & founder-centric)
|
||||
|
||||
**Team**
|
||||
- Market validation
|
||||
- GitHub contribution
|
||||
- Track record (incl. red flag projects)
|
||||
|
||||
**Financials**
|
||||
- Investments
|
||||
- TVL (like Aztec's L2)
|
||||
- Donation-based
|
||||
- Public treasury
|
||||
|
||||
**Liveliness**
|
||||
- How active is GitHub activity
|
||||
- How active is the community
|
||||
- Is there public product traction?
|
||||
|
||||
**Product-readiness**
|
||||
- State of product-readiness
|
||||
- MVP-readiness
|
||||
- Protocol (test-net/main-net)
|
||||
- dApp (release timing, third-party validation like AppStore/Play Store)
|
||||
- network-reliability (the state of privacy in Ethereum, Solana, Avalanche etc)
|
||||
|
||||
**Cross-checked data leakage**
|
||||
- Complementing privacy stack data leakage (example: phone + dApp; wallet + RPC etc)
|
||||
- Third-party data leakage (from the hackers to state agents (think of Iran or North Korean govs))
|
||||
|
||||
**Data aggregation policies**
|
||||
|
||||
_Reference_: https://tosdr.org
|
||||
|
||||
**Centralisation level (incl KYC)**
|
||||
|
||||
Reference: https://kycnot.me/about#scores
|
||||
BIN
Web3privacynowplatform/Staticobjects/Platform MVP components.png
Normal file
|
After Width: | Height: | Size: 274 KiB |
1
Web3privacynowplatform/Staticobjects/Readme.md
Normal file
|
|
@ -0,0 +1 @@
|
|||
Repo for imgs
|
||||
|
After Width: | Height: | Size: 245 KiB |
|
After Width: | Height: | Size: 75 KiB |
|
After Width: | Height: | Size: 37 KiB |
|
After Width: | Height: | Size: 35 KiB |
|
After Width: | Height: | Size: 83 KiB |
|
After Width: | Height: | Size: 63 KiB |
|
After Width: | Height: | Size: 195 KiB |
|
After Width: | Height: | Size: 154 KiB |
|
After Width: | Height: | Size: 110 KiB |
|
After Width: | Height: | Size: 229 KiB |
|
After Width: | Height: | Size: 189 KiB |
|
After Width: | Height: | Size: 323 KiB |
|
After Width: | Height: | Size: 508 KiB |
|
After Width: | Height: | Size: 1 MiB |
|
After Width: | Height: | Size: 143 KiB |
|
After Width: | Height: | Size: 242 KiB |
|
After Width: | Height: | Size: 82 KiB |
|
After Width: | Height: | Size: 86 KiB |
|
After Width: | Height: | Size: 189 KiB |
|
After Width: | Height: | Size: 141 KiB |
|
After Width: | Height: | Size: 11 KiB |
|
After Width: | Height: | Size: 1.2 MiB |
|
After Width: | Height: | Size: 469 KiB |
|
After Width: | Height: | Size: 268 KiB |
|
After Width: | Height: | Size: 209 KiB |
|
After Width: | Height: | Size: 1.4 MiB |
|
After Width: | Height: | Size: 198 KiB |
|
After Width: | Height: | Size: 665 KiB |
|
After Width: | Height: | Size: 304 KiB |
|
After Width: | Height: | Size: 244 KiB |
|
After Width: | Height: | Size: 235 KiB |
|
After Width: | Height: | Size: 73 KiB |
|
After Width: | Height: | Size: 77 KiB |
|
After Width: | Height: | Size: 422 KiB |
1
Web3privacynowplatform/Staticobjects/UI/Readme.md
Normal file
|
|
@ -0,0 +1 @@
|
|||
|
||||
BIN
Web3privacynowplatform/Staticobjects/Visual prototype.png
Normal file
|
After Width: | Height: | Size: 234 KiB |
68
Web3privacynowplatform/UI/Readme.md
Normal file
|
|
@ -0,0 +1,68 @@
|
|||
# User interfaces
|
||||
|
||||
Here we highlight iterations of platform UI
|
||||
|
||||
**UI delivery summary, 2.11**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Platform%20UI%20delivery%2C%202.11.png" width="900"/>
|
||||
|
||||
**UI-readiness delivery**
|
||||
|
||||
1. [V1.0: ETH Rome prototype](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/UI/Readme.md#v10-eth-rome-prototype)
|
||||
|
||||
2. [V1.1: post-ETHRome update V1.1: post-ETHRome update](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/UI/Readme.md#v11-post-ethrome-update)
|
||||
|
||||
3. [V1.1: post-ETHRome update (mobile version) V1.1: post-ETHRome update (mobile version)](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/UI/Readme.md#v11-post-ethrome-update-mobile-version)
|
||||
|
||||
4. [V1.2: post-ETHRome update (basic scoring x brief sync) V1.2: post-ETHRome update (basic scoring x brief sync)](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/UI/Readme.md#v12-post-ethrome-update-basic-scoring-x-brief-sync)
|
||||
|
||||
5. [V1.0: post-ETH Rome asset router microservice V1.0: post-ETH Rome asset router microservice](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/UI/Readme.md#v10-post-eth-rome-asset-router-microservice)
|
||||
|
||||
## V1.0: ETH Rome prototype
|
||||
|
||||
**Privacy services DB x scoring (ETHRome build)**
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%20(ETH%20Rome%20build).png" width="700"/>
|
||||
|
||||
**Privacy services DB x scoring, alt version (ETHRome build)**
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%2C%20v2%20(ETH%20Rome%20build).png" width="700"/>
|
||||
|
||||
**Privacy service full profile (ETHRome build)**
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20service%20full%20profile%20(ETH%20Rome%20build).png" width="700"/>
|
||||
|
||||
## V1.1: post-ETHRome update
|
||||
|
||||
**Privacy services DB x scoring**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%201.1.png" width="700"/>
|
||||
|
||||
**Privacy services DB x scoring, alt version**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%201.1%20(2).png" width="700"/>
|
||||
|
||||
## V1.1: post-ETHRome update (mobile version)
|
||||
|
||||
**Privacy services DB x scoring (mobile)**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%20(mobile).png" width="500"/>
|
||||
|
||||
**Privacy service full profile (mobile, short)**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20service%20full%20profile%20(mobile%2C%20short).png" width="500"/>
|
||||
|
||||
## V1.2: post-ETHRome update (basic scoring x brief sync)
|
||||
|
||||
**Railgun_ profile scored x brief (mobile, short)**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%20x%20brief%20(mobile).png" width="500"/>
|
||||
|
||||
**Railgun_ profile scored x brief (desktop, short)**
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Privacy%20services%20DB%20x%20scoring%20x%20brief%20(desktop).png" width="500"/>
|
||||
|
||||
# Bonus
|
||||
|
||||
## V1.0: post-ETH Rome asset router microservice
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Asset%20router%20microservice%20prototype.png" width="700"/>
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Asset%20router%20microservice%20prototype2.png" width="700"/>
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Staticobjects/UI/Asset%20router%20microservice%20prototype3.png" width="700"/>
|
||||
|
|
@ -0,0 +1,215 @@
|
|||
## Here we compare data brief to fill for privacy companies via Pull request at GitHub (source of latest updates within the market) & our scoring MVP
|
||||
What could be scored in general & with am MVP specifically.
|
||||
|
||||
**Sandbox**
|
||||
- [Basic info from the Brief](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Brief.md#basic-info)
|
||||
- [Optional info from the Brief](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Brief.md#optional-info)_ covers generic data for privacy service "profile page" (beyond just privacy features)
|
||||
- _Scoring_ - possible non-techies' independent assessment (future version): + - yes, - no
|
||||
- _[MVP](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Framework_update.md)_ - what lies within the scope of the first scoring version: :white_check_mark: - yes
|
||||
|
||||
**Basic info**
|
||||
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Launch date** | + | :white_check_mark: |
|
||||
| **Is it open source?** | + | - |
|
||||
| **Website** | + | :white_check_mark: |
|
||||
| **Github** | + | :white_check_mark: |
|
||||
|
||||
**Token**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Do you have a token** | - | - |
|
||||
|
||||
**Socials**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Blog** | - | :white_check_mark: |
|
||||
| **Twitter (X)** | + | :white_check_mark: |
|
||||
| **Telegram** | + | :white_check_mark: |
|
||||
| **Discord** | + | :white_check_mark: |
|
||||
| **Other** | + | :white_check_mark: |
|
||||
|
||||
**Docs**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Docs** | + | :white_check_mark: |
|
||||
| **Whitepaper** | + | :white_check_mark: |
|
||||
| **Litepaper** | + | - |
|
||||
|
||||
**Team**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Is your team anon or public** | + | :white_check_mark: |
|
||||
| **List core contributors** | + | :white_check_mark: |
|
||||
|
||||
**Funding**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **How are you funded** | - | - |
|
||||
| **List VCs backing you** | - | - |
|
||||
| **List VCs round** | - | - |
|
||||
| **Raised money** | - | - |
|
||||
|
||||
**Github**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **What licence is in use** | + | - |
|
||||
|
||||
**Technology**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Technical specialisation** | - | - |
|
||||
| **Specify technology readiness** | + | :white_check_mark: |
|
||||
| **Features** | - | - |
|
||||
| **Encryption method** | - | - |
|
||||
|
||||
**Privacy**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Is it peer-to-peer** | + | - |
|
||||
| **Complience** | + | - |
|
||||
| **KYC** | + | - |
|
||||
| **Privacy policy** | + | - |
|
||||
| **Collected data** | + | - |
|
||||
| **Data sharing** | + | - |
|
||||
| **Sign-in requirments** | + | - |
|
||||
| **Identity integrations** | + | - |
|
||||
|
||||
**Security**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Asset custody** | + | - |
|
||||
| **Upgradability** | + | - |
|
||||
| **Social dependency** | + | - |
|
||||
| **Third-parties dependency** | + | - |
|
||||
| **Technical dependency** | + | - |
|
||||
| **Have you been audited by a third-party** | + | :white_check_mark: |
|
||||
| **What company audited** | + | :white_check_mark: |
|
||||
| **When you were audited** | + | :white_check_mark: |
|
||||
| **Add links to the audits** | + | :white_check_mark: |
|
||||
|
||||
**Roadmap (technical)**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **When product had been launched** | + | :white_check_mark: |
|
||||
| **When mainnet, beta had been launched** | + | :white_check_mark: |
|
||||
|
||||
# MVP
|
||||
Here we cover scope within scoring MVP
|
||||
|
||||
**Basic info**
|
||||
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **Launch date** | :white_check_mark: |
|
||||
| **Website** | :white_check_mark: |
|
||||
| **Github** | :white_check_mark: |
|
||||
|
||||
**Socials**
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **Blog** | :white_check_mark: |
|
||||
| **Twitter (X)** | :white_check_mark: |
|
||||
| **Telegram** | :white_check_mark: |
|
||||
| **Discord** | :white_check_mark: |
|
||||
| **Other** | :white_check_mark: |
|
||||
|
||||
**Docs**
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **Docs** | :white_check_mark: |
|
||||
| **Whitepaper** | :white_check_mark: |
|
||||
|
||||
**Team**
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **Is your team anon or public** | :white_check_mark: |
|
||||
| **List core contributors** | :white_check_mark: |
|
||||
|
||||
**Technology**
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **Specify technology readiness** | :white_check_mark: |
|
||||
|
||||
**Security**
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **Have you been audited by a third-party** | :white_check_mark: |
|
||||
| **What company audited** | :white_check_mark: |
|
||||
| **When you were audited** | :white_check_mark: |
|
||||
| **Add links to the audits** | :white_check_mark: |
|
||||
|
||||
**Roadmap (technical)**
|
||||
| Brief | MVP |
|
||||
| ------------- | ------------- |
|
||||
| **When product had been launched** | :white_check_mark: |
|
||||
| **When mainnet, beta had been launched** | :white_check_mark: |
|
||||
|
||||
**Total data sets: 19**
|
||||
|
||||
# Full scoring scope of work
|
||||
Here we cover scope that's beyond MVP & is necessary to develop the next versions of the scoring framework.
|
||||
|
||||
**Basic info**
|
||||
|
||||
| Brief | Scoring |
|
||||
| ------------- | ------------- |
|
||||
| **Is it open source?** | + |
|
||||
|
||||
**Docs**
|
||||
| Brief | Scoring |
|
||||
| ------------- | ------------- |
|
||||
| **Litepaper** | + |
|
||||
|
||||
**Github**
|
||||
| Brief | Scoring |
|
||||
| ------------- | ------------- |
|
||||
| **What licence is in use** | + |
|
||||
|
||||
**Privacy**
|
||||
| Brief | Scoring |
|
||||
| ------------- | ------------- |
|
||||
| **Is it peer-to-peer** | + |
|
||||
| **Complience** | + |
|
||||
| **KYC** | + |
|
||||
| **Privacy policy** | + |
|
||||
| **Collected data** | + |
|
||||
| **Data sharing** | + |
|
||||
| **Sign-in requirments** | + |
|
||||
| **Identity integrations** | + |
|
||||
|
||||
**Security**
|
||||
| Brief | Scoring |
|
||||
| ------------- | ------------- |
|
||||
| **Asset custody** | + |
|
||||
| **Upgradability** | + |
|
||||
| **Social dependency** | + |
|
||||
| **Third-parties dependency** | + |
|
||||
| **Technical dependency** | + |
|
||||
|
||||
**Total data sets: 16**
|
||||
|
||||
# Out of scope
|
||||
|
||||
**Basic info**
|
||||
|
||||
**Token**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Do you have a token** | - | - |
|
||||
|
||||
**Funding**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **How are you funded** | - | - |
|
||||
| **List VCs backing you** | - | - |
|
||||
| **List VCs round** | - | - |
|
||||
| **Raised money** | - | - |
|
||||
|
||||
**Technology**
|
||||
| Brief | Scoring | MVP |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| **Technical specialisation** | - | - |
|
||||
| **Privacy features** | - | - |
|
||||
| **Encryption method** | - | - |
|
||||
395
Web3privacynowplatform/scoringmodel/DeFi category prototype.md
Normal file
|
|
@ -0,0 +1,395 @@
|
|||
# Scoring model testing repo
|
||||
|
||||
_Here we test the latest scoring approach for non-techies (30 Oct, 2023) whenever service is private or not._
|
||||
|
||||
[Applied scoring approach](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/E9QPx9iKgPXPqEsAN-YklipSRJy9VTBMOLwwEcqqVpU)
|
||||
|
||||
**Simplified overview**
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test project** | available & active GitHub / not (25%) | Live or 🚧 (exclusion criteria) | public team / not (25%) | available & not marketing docs / not (25%) | available & up to date third-party audit / not (25%) | total |
|
||||
| -> | 25% | 🚧 | 25% | 25% | 25% | from 0% to 100% |
|
||||
|
||||
**Note**:
|
||||
- persona: non-techie
|
||||
- max score: 100% (public GitHub, third-party audit, public Docs, public team)
|
||||
- min score: 0%
|
||||
- 🚩 - represents project sunset, empty or inactive Github, marketing docs
|
||||
- 🚧 - represents that the project is not live on mainnet, this is an exclusion criteria that forces project score to be 0%
|
||||
|
||||
## DeFi
|
||||

|
||||
|
||||
**Total**: 38 projects
|
||||
|
||||
| Project | Description | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- | ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Firn Protocol](https://app.firn.cash) | Firn is the first-ever zero-knowledge privacy platform in the _account-based_ model, and introduces pluggable, flexible privacy to Ethereum-based chains. ✨️**ZK** | ([GitHub](https://github.com/firnprotocol)) | live | anon | [Docs](https://docs.firn.cash) | [BlockSec](https://github.com/blocksecteam/audit-reports/blob/main/solidity/blocksec_firnprotocol_v1.0-signed.pdf) | 75% |
|
||||
| [Shade](https://shadeprotocol.io) | Shade Protocol is an array of connected privacy-preserving DeFi applications built on Secret Network | ([GitHub](https://github.com/securesecrets/shade)) | live | anon | [Docs](https://docs.shadeprotocol.io/shade-protocol/) | 🚩 2022: [2 audits](https://docs.shadeprotocol.io/shade-protocol/research/audit-log) | 75% |
|
||||
| [Silent protocol](https://www.silentprotocol.org) | Silent Protocol is the first protocol enabling compliant full-stack privacy for smart contract assets and web3 applications at scale. | - | 🚧 | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [XATA](https://www.xata.fi) | A MEV Minimization solution to survive the Dark Forest | - | 🚩 | anon | ([Docs](https://docs.xata.fi)) | - | 25% |
|
||||
| [Sienna Network](https://sienna.network) | Sienna is a privacy-first and cross-chain decentralized finance platform where you can privately swap, lend and convert your tokens into their private equivalent | 🚩`LOW` ([GitHub](https://github.com/SiennaNetwork)) | 🚧 | anon | [Docs](https://docs.sienna.network/main/) | 🚩 2022: [9 audits](https://sienna.network/audits/) | 75% |
|
||||
| [Elusiv](https://elusiv.io) | Create blockchain privacy solutions that are built for everyday transactions — with the power of scalable ZK infrastructure on Solana ✨️**ZK** | ([GitHub](https://github.com/elusiv-privacy)) | live | ([Public](https://www.linkedin.com/search/results/people/?currentCompany=%5B%2280778213%22%5D&origin=COMPANY_PAGE_CANNED_SEARCH&sid=s_%40)) | 🚩 **marketing** [Docs](https://docs.elusiv.io/) | - | 75% |
|
||||
| [Offshift](https://www.offshift.io) | Offshift’s proprietary Shifting mechanism allows users to Shift between our native token, XFT, and a full palette of private synthetics | 🚩 **LOW** ([GitLab](https://open.offshift.io/offshiftXFT)) | live | ([anon](https://offshift.io/#team)) | - | - | 25% |
|
||||
| [CAPE](https://www.espressosys.com/product) | Configurable Asset Privacy for Ethereum | ([GitHub](https://github.com/EspressoSystems/cape)) | 🚧 | anon | [Docs](https://docs.espressosys.com/sequencer/espresso-sequencer-architecture/readme) | - | 50% |
|
||||
| [Evanesco](https://evanesco.org) | A financial protocol platform that combines Layer0 network infrastructure with a private computing framework. | ([GitHub](https://github.com/Evanesco-Labs)) | live | anon | - | - | 25% |
|
||||
| [Dusk Network](https://dusk.network) | Is technology for securities. An open source and secure blockchain (DLT) infrastructure that businesses use to tokenize financial instruments and automate costly processes. | ([GitHub](https://github.com/dusk-network)) | 🚧 | ([Public](https://dusk.network/pages/team)) | - | - | 50% |
|
||||
| [Manta Pay](https://app.manta.network/dolphin/transact) | MantaPay is coming to Calamari as the first privacy payment solution in the Kusama ecosystem.✨️**ZK** | ([GitHub](https://github.com/Manta-Network)) | testnet v3 | public | [Docs](https://docs.manta.network/docs/Introduction) | - | 75% |
|
||||
| [Webb](https://app.webb.tools/#/tornado) | an interoperable private bridge ✨️**ZK** | ([GitHub](https://github.com/webb-tools)) | 🚧 | anon | [Docs](https://docs.webb.tools/docs/) | [Audit of the DKG-Substrate pallet](https://blog.webb.tools/webbs-evm-bridge-security-audit-completed-by-veridise/) | 75% |
|
||||
| [Panther Protocol](https://www.pantherprotocol.io) | is a decentralized privacy metaprotocol enabling confidential, trusted transactions and interoperability with DeFi ✨️**ZK** | ([GitHub](https://github.com/pantherprotocol)) | live | ([Public](https://www.pantherprotocol.io/)) | [Docs](https://docs.pantherprotocol.io/docs/start-here/panther-protocol-documentation) | 🚩 2021: [ZKP Vesting](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Vesting.pdf), [ZKP Token](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Token.pdf) | 100% |
|
||||
| 🚩 **sunset** [zk.money](https://zk.money) | The private DeFi yield aggregator for Ethereum.✨️**ZK** | ([Docs](https://docs.aztec.network/zk-money/userguide)) | 🚩 | anon | [Docs](https://docs.aztec.network) | - | 25% |
|
||||
| [RAILGUN](https://railgun.org) | Private transfers and DeFi infra for Ethereum, Polygon, Binance Smart Chain and Arbitrum.✨️**ZK** | [Github](https://github.com/Railgun-Community) | live | ([Public](https://railgun.org/#/contributors)) | [Docs](https://docs.railgun.org/developer-guide/cookbook/cookbook-overview) | [5 audits](https://assets.railgun.org/docs/audits/) | 100% |
|
||||
| [Umbra](https://app.umbra.cash) | As a protocol, Umbra defines a simple set of standards, coupled with a singleton smart contract instance, to enable stealth addresses on Ethereum | ([GitHub](https://github.com/ScopeLift/umbra-protocol)) | live | anon | - | 🚩 2021: [3 audits](https://app.umbra.cash/faq#security) | 50% |
|
||||
| [Light Shield](https://shield.lightprotocol.com) | private transactions for Solana. | - | live | anon | [Docs](https://docs.lightprotocol.com) | 🚩 2022: [Code review](https://github.com/Lightprotocol/light-protocol-v1/blob/main/Audit/Light%20Protocol%20Audit%20Report.pdf) | 50% |
|
||||
| [Horizon](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | Decentralized Anonymous Payment Systems ✨️**ZK** | - | 🚧 | anon | 🚩 **marketing** [Docs](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | [Messier](https://skynet.certik.com/projects/messier) | 50% |
|
||||
| [Diva](https://www.diva.exchange/en/) | Free banking technology for everyone: everyone can join in, everyone can use DIVA.EXCHANGE | ([GitHub](https://github.com/diva-exchange)) | 🚧 | - | ([Public](https://www.diva.exchange/en/team-and-contact/)) | [Docs](https://docs.lightprotocol.com) | - | - | 75% |
|
||||
| 🚩 **sunset** [Yellow Submarine](https://ys.finance) | the first and only multichain dApp to offer plug-and-play private DeFi (PriFi) across all EVM-compatible chains | ([Docs](https://yellow-s.gitbook.io/docs/ys-basics/introduction)) | 🚩 | anon | - | - | 25% |
|
||||
| [BasicSwap](https://basicswapdex.com) | Private Cross-Chain DEX | ([GitHub](https://github.com/tecnovert/basicswap/blob/master/doc/install.md)) | live | ([anon](https://particl.io/)) | - | - | 50% |
|
||||
| [Common](https://common.fi) | Common will be a decentralized exchange that mitigates the Maximal Extractable Value (MEV) problem. | - | 🚧 | anon | - | - | 0% |
|
||||
| [Sacred](https://sacred.finance) | multi-chain DeFi Platform offers private Yield Bearing Deposits to DeFi users ✨️**ZK* | 🚩 **LOW** ([GitHub](https://github.com/Sacred-Finance)) | 🚧 | Ethereum, Polygon | anon | - | - | 25% |
|
||||
| 🚩 **sunset** [Sahara](https://sahara.network) | The first dedicated privacy protocol ecosystem that enables on-platform trade between volatile and stable assets | - | 🚩 | ([Public](https://sahara.network/)) | - | 🚩 2022: [Vesting contract](https://sahara.network/resources/sahara-security-audit.pdf) | 50% |
|
||||
| 🚩 **sunset** [DeFiner](https://definer.org) | Permission-less and configurable decentralized lending protocol with privacy 100% protected ✨️**ZK** | ([GitHub](https://github.com/DeFinerOrg)) | 🚩 | anon | [Docs](https://docs.definer.org) | 🚩 2020: [Savings audits](https://docs.definer.org/v/copy-of-definer.org/security/audits) | 75% |
|
||||
| [Hurricane Protocol](https://hurricane.money) | A fully decentralized protocol offering private transactions on both the Terra & NEAR | 🚩 **no code** ([GitHub](https://github.com/Hurricane-Protocol)) | 🚧 | anon | 🚩 **marketing** [Docs](https://docs.hurricane.money) | - | 50% |
|
||||
| [StealthPay](https://www.stealthpay.cash) | a stealth address protocol for Ethereum.| 🚩 **dead** ([GitHub](https://github.com/cryptoadong)) | 🚩 | anon | - | - | 25% |
|
||||
| [BlackBox](https://blackbox.cash) | collection of tools allowing you send & receive SCRT anonymously | ([GitHub](https://github.com/TriviumNode)) | 🚧 | anon | - | - | 25% |
|
||||
| [Hinkal](https://hinkal.pro) | an easy-to-integrate privacy SDK that helps users anonymize transactions. | - | live | ([Public](https://hinkal.pro/#section-team)) | - | [Competitive security](https://github.com/Secure3Audit/Secure3Academy/blob/main/audit_reports/Hinkal/Hinkal_final_Secure3_Audit_Report.pdf) | 50% |
|
||||
| [Conceal Network](https://conceal.network) | privacy-protected DeFi & encrypted comms | ([GitHub](https://github.com/ConcealNetwork)) | live | ([anon](https://conceal.network/team/)) | [Docs](https://conceal.network/wiki/doku.php) | - | 50% |
|
||||
| [CIA protocol](https://ciaprotocol.com) | Building the truest form of DeFi with privacy by default. | - | 🚧 | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [CoinBook](https://www.coinbook.app) | Decentralized Multi Chain P2P Order Book | - | 🚩 | anon | - | - | 0% |
|
||||
| [Seven Seas](https://www.sevenseas.exchange) | No KYC, privacy Focused crypto Exchange | - | 🚧 | - | - | - | 0% |
|
||||
| [NonKYC](https://nonkyc.io) | NonKYC Exchange | - | - | 🚧 | - | - | - | 0% |
|
||||
| [zkUSD](https://zkusd.money/#Features) | Privacy-Preserving Collateralized Lending & more | 🚩 | 🚩 **no code** ([GitHub](https://github.com/zkUSDLabs)) | - | - | 🚩 **marketing** [Docs](https://zkusd.gitbook.io/zkusd-documentation) | - | 50% |
|
||||
| [Spiral Finance](https://www.spiralfi.io) | non-custodial privacy solution based on ZK-Sync ERA ✨️**ZK** | - | 🚧 | - | ([Docs](https://docs.spiralfi.io/introduction/spiral-finance)) | - | 25% |
|
||||
| [Fairy](https://fairyswap.finance/swap) | comprehensive DeFi platform for token swaps, lending, NFT trading, collateralization | 🚩 **dead** ([GitHub](https://github.com/Fairyswap)) | 🚩 | - | [Docs](https://fairy-swap.gitbook.io/fairyswap-v2/getting-started/about-fairyswap-v2) | 🚩 2022: [Certik](https://skynet.certik.com/projects/fairyswap) | 75% |
|
||||
| [Shade Cash](https://shade.cash) | A decentralized protocol for private transactions on Fantom Opera | 🚩 **no code** ([GitHub](https://github.com/ShadeCash)) | 🚩 | - | 🚩 **marketing** [Docs](https://shadecash.gitbook.io/shadecash) | - | 50% |
|
||||
|
||||
# Post-assesment breakdown
|
||||
|
||||
## 100% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- |------------- | ------------- | ------------- | ------------- |
|
||||
| [Panther Protocol](https://www.pantherprotocol.io) | ([GitHub](https://github.com/pantherprotocol)) | live | ([Public](https://www.pantherprotocol.io/)) | [Docs](https://docs.pantherprotocol.io/docs/start-here/panther-protocol-documentation) | 🚩 2021: [ZKP Vesting](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Vesting.pdf), [ZKP Token](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Token.pdf) | 100% |
|
||||
| [RAILGUN](https://railgun.org) | [Github](https://github.com/Railgun-Community) | live | ([Public](https://railgun.org/#/contributors)) | [Docs](https://docs.railgun.org/developer-guide/cookbook/cookbook-overview) | [5 audits](https://assets.railgun.org/docs/audits/) | 100% |
|
||||
|
||||
**total**: 2 projects
|
||||
|
||||
**Details**:
|
||||
- 1 red flag 🚩
|
||||
|
||||
## 75% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Firn Protocol](https://app.firn.cash) | ([GitHub](https://github.com/firnprotocol)) | live | anon | [Docs](https://docs.firn.cash) | [BlockSec](https://github.com/blocksecteam/audit-reports/blob/main/solidity/blocksec_firnprotocol_v1.0-signed.pdf) | 75% |
|
||||
| [Shade](https://shadeprotocol.io) | ([GitHub](https://github.com/securesecrets/shade)) | live | anon | [Docs](https://docs.shadeprotocol.io/shade-protocol/) | 🚩 2022: [2 audits](https://docs.shadeprotocol.io/shade-protocol/research/audit-log) | 75% |
|
||||
| [Sienna Network](https://sienna.network) | 🚩`LOW` ([GitHub](https://github.com/SiennaNetwork)) | 🚧 | anon | [Docs](https://docs.sienna.network/main/) | 🚩 2022: [9 audits](https://sienna.network/audits/) | 75% |
|
||||
| [Elusiv](https://elusiv.io) | ([GitHub](https://github.com/elusiv-privacy)) | live | ([Public](https://www.linkedin.com/search/results/people/?currentCompany=%5B%2280778213%22%5D&origin=COMPANY_PAGE_CANNED_SEARCH&sid=s_%40)) | 🚩 **marketing** [Docs](https://docs.elusiv.io/) | - | 75% |
|
||||
| [Manta Pay](https://app.manta.network/dolphin/transact) | ([GitHub](https://github.com/Manta-Network)) | 🚧 | public | [Docs](https://docs.manta.network/docs/Introduction) | - | 75% |
|
||||
| [Webb](https://app.webb.tools/#/tornado) | ([GitHub](https://github.com/webb-tools)) | 🚧 | anon | [Docs](https://docs.webb.tools/docs/) | [Audit of the DKG-Substrate pallet](https://blog.webb.tools/webbs-evm-bridge-security-audit-completed-by-veridise/) | 75% |
|
||||
| [Diva](https://www.diva.exchange/en/) | ([GitHub](https://github.com/diva-exchange)) | 🚧 | ([Public](https://www.diva.exchange/en/team-and-contact/)) | [Docs](https://docs.lightprotocol.com) | - | - | 75% |
|
||||
| 🚩 **sunset** [DeFiner](https://definer.org) | ([GitHub](https://github.com/DeFinerOrg)) | 🚩 | anon | [Docs](https://docs.definer.org) | 🚩 2020: [Savings audits](https://docs.definer.org/v/copy-of-definer.org/security/audits) | 75% |
|
||||
| [Fairy](https://fairyswap.finance/swap) | 🚩 **dead** ([GitHub](https://github.com/Fairyswap)) | 🚩 | - | [Docs](https://fairy-swap.gitbook.io/fairyswap-v2/getting-started/about-fairyswap-v2) | 🚩 2022: [Certik](https://skynet.certik.com/projects/fairyswap) | 75% |
|
||||
|
||||
**total**: 9 projects
|
||||
|
||||
**Details**:
|
||||
- 7 red flags 🚩
|
||||
- 1 sunset
|
||||
|
||||
## 50% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [CAPE](https://www.espressosys.com/product) | ([GitHub](https://github.com/EspressoSystems/cape)) | testnet | anon | [Docs](https://docs.espressosys.com/sequencer/espresso-sequencer-architecture/readme) | - | 50% |
|
||||
| [Dusk Network](https://dusk.network) | ([GitHub](https://github.com/dusk-network)) | 🚧 | ([Public](https://dusk.network/pages/team)) | - | - | 50% |
|
||||
| [Umbra](https://app.umbra.cash) | ([GitHub](https://github.com/ScopeLift/umbra-protocol)) | live | anon | - | 🚩 2021: [3 audits](https://app.umbra.cash/faq#security) | 50% |
|
||||
| [Light Shield](https://shield.lightprotocol.com) | - | live | anon | [Docs](https://docs.lightprotocol.com) | 🚩 2022: [Code review](https://github.com/Lightprotocol/light-protocol-v1/blob/main/Audit/Light%20Protocol%20Audit%20Report.pdf) | 50% |
|
||||
| [Horizon](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | - | 🚧 | anon | 🚩 **marketing** [Docs](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | [Messier](https://skynet.certik.com/projects/messier) | 50% |
|
||||
| [BasicSwap](https://basicswapdex.com) | ([GitHub](https://github.com/tecnovert/basicswap/blob/master/doc/install.md)) | live | ([anon](https://particl.io/)) | - | - | 50% |
|
||||
| 🚩 **sunset** [Sahara](https://sahara.network) | - | 🚩 | ([Public](https://sahara.network/)) | - | 🚩 2022: [Vesting contract](https://sahara.network/resources/sahara-security-audit.pdf) | 50% |
|
||||
| [Hurricane Protocol](https://hurricane.money) | 🚩 **no code** ([GitHub](https://github.com/Hurricane-Protocol)) | 🚧 | anon | 🚩 **marketing** [Docs](https://docs.hurricane.money) | - | 50% |
|
||||
| [Hinkal](https://hinkal.pro) | - | live | ([Public](https://hinkal.pro/#section-team)) | - | [Competitive security](https://github.com/Secure3Audit/Secure3Academy/blob/main/audit_reports/Hinkal/Hinkal_final_Secure3_Audit_Report.pdf) | 50% |
|
||||
| [Conceal Network](https://conceal.network) | ([GitHub](https://github.com/ConcealNetwork)) | live | ([anon](https://conceal.network/team/)) | [Docs](https://conceal.network/wiki/doku.php) | - | 50% |
|
||||
| [zkUSD](https://zkusd.money/#Features) | 🚩 **no code** ([GitHub](https://github.com/zkUSDLabs)) | 🚧 | - | - | 🚩 **marketing** [Docs](https://zkusd.gitbook.io/zkusd-documentation) | - | 50% |
|
||||
| [Shade Cash](https://shade.cash) | 🚩 **no code** ([GitHub](https://github.com/ShadeCash)) | 🚧 | - | - | 🚩 **marketing** [Docs](https://shadecash.gitbook.io/shadecash) | - | 50% |
|
||||
|
||||
**total**: 12 projects
|
||||
|
||||
**Details**:
|
||||
- 11 red flags 🚩
|
||||
- 1 sunset
|
||||
|
||||
## 25% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- |------------- | ------------- | ------------- | ------------- |
|
||||
| 🚩 **sunset** [XATA](https://www.xata.fi) | - | 🚩 | anon | ([Docs](https://docs.xata.fi)) | - | 25% |
|
||||
| [Offshift](https://www.offshift.io) | 🚩 **LOW** ([GitLab](https://open.offshift.io/offshiftXFT)) | live | ([anon](https://offshift.io/#team)) | - | - | 25% |
|
||||
| [Evanesco](https://evanesco.org) | ([GitHub](https://github.com/Evanesco-Labs)) | live | anon | - | - | 25% |
|
||||
| 🚩 **sunset** [zk.money](https://zk.money) | ([Docs](https://docs.aztec.network/zk-money/userguide)) | 🚩 | anon | [Docs](https://docs.aztec.network) | - | 25% |
|
||||
| 🚩 **sunset** [Yellow Submarine](https://ys.finance) | ([Docs](https://yellow-s.gitbook.io/docs/ys-basics/introduction)) | 🚩 | anon | - | - | 25% |
|
||||
| [Sacred](https://sacred.finance) | 🚩 **LOW** ([GitHub](https://github.com/Sacred-Finance)) | 🚧 | anon | - | - | 25% |
|
||||
| [StealthPay](https://www.stealthpay.cash) | 🚩 **dead** ([GitHub](https://github.com/cryptoadong)) | 🚧 | anon | - | - | 25% |
|
||||
| [BlackBox](https://blackbox.cash) | ([GitHub](https://github.com/TriviumNode)) | 🚧 | anon | - | - | 25% |
|
||||
| [Spiral Finance](https://www.spiralfi.io) | - | 🚧 | - | ([Docs](https://docs.spiralfi.io/introduction/spiral-finance)) | - | 25% |
|
||||
|
||||
**total**: 9 projects
|
||||
|
||||
**Details**:
|
||||
- 6 red flags 🚩
|
||||
- 3 sunsets
|
||||
|
||||
## 0% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- |------------- | ------------- | ------------- | ------------- |
|
||||
| [Silent protocol](https://www.silentprotocol.org) | - | 🚧 | anon | - | - | 0% |
|
||||
| [Common](https://common.fi) | - | 🚧 | anon | - | - | 0% |
|
||||
| [CIA protocol](https://ciaprotocol.com) | - | 🚧 | Ethereum | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [CoinBook](https://www.coinbook.app) | - | 🚩 | anon | - | - | 0% |
|
||||
| [Seven Seas](https://www.sevenseas.exchange) | - | 🚧 | - | - | - | - | - | 0% |
|
||||
| [NonKYC](https://nonkyc.io) | - | 🚧 | - | - | - | - | - | 0% |
|
||||
|
||||
**total**: 6 projects
|
||||
|
||||
**Details**:
|
||||
- 1 red flag 🚩
|
||||
- 1 sunset
|
||||
|
||||
# Red-flag applicable breakdown
|
||||
|
||||
**Note**:
|
||||
- 🚩 - represents - 25% of scoring
|
||||
- sunset - decreases scoring to 0%
|
||||
|
||||
## 100% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [RAILGUN](https://railgun.org) | [Github](https://github.com/Railgun-Community) | live | ([Public](https://railgun.org/#/contributors)) | [Docs](https://docs.railgun.org/developer-guide/cookbook/cookbook-overview) | [5 audits](https://assets.railgun.org/docs/audits/) | 100% |
|
||||
|
||||
**total**: 1 project
|
||||
|
||||
## 75% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- | ------------ | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Firn Protocol](https://app.firn.cash) | ([GitHub](https://github.com/firnprotocol)) | live | anon | [Docs](https://docs.firn.cash) | [BlockSec](https://github.com/blocksecteam/audit-reports/blob/main/solidity/blocksec_firnprotocol_v1.0-signed.pdf) | 75% |
|
||||
| [Manta Pay](https://app.manta.network/dolphin/transact) | ([GitHub](https://github.com/Manta-Network)) | 🚧 | public | [Docs](https://docs.manta.network/docs/Introduction) | - | 75% |
|
||||
| [Webb](https://app.webb.tools/#/tornado) | ([GitHub](https://github.com/webb-tools)) | 🚧 | anon | [Docs](https://docs.webb.tools/docs/) | [Audit of the DKG-Substrate pallet](https://blog.webb.tools/webbs-evm-bridge-security-audit-completed-by-veridise/) | 75% |
|
||||
| [Diva](https://www.diva.exchange/en/) | ([GitHub](https://github.com/diva-exchange)) | 🚧 | ([Public](https://www.diva.exchange/en/team-and-contact/)) | [Docs](https://docs.lightprotocol.com) | - | - | 75% |
|
||||
| [Panther Protocol](https://www.pantherprotocol.io) | ([GitHub](https://github.com/pantherprotocol)) | live | ([Public](https://www.pantherprotocol.io/)) | [Docs](https://docs.pantherprotocol.io/docs/start-here/panther-protocol-documentation) | 🚩 2021: [ZKP Vesting](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Vesting.pdf), [ZKP Token](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Token.pdf) | 75% |
|
||||
|
||||
**total**: 5 projects
|
||||
|
||||
**Details**:
|
||||
- 1 red flag 🚩
|
||||
|
||||
## 50% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [CAPE](https://www.espressosys.com/product) | ([GitHub](https://github.com/EspressoSystems/cape)) | 🚧 | anon | [Docs](https://docs.espressosys.com/sequencer/espresso-sequencer-architecture/readme) | - | 50% |
|
||||
| [Dusk Network](https://dusk.network) | ([GitHub](https://github.com/dusk-network)) | 🚧 | ([Public](https://dusk.network/pages/team)) | - | - | 50% |
|
||||
| [BasicSwap](https://basicswapdex.com) | ([GitHub](https://github.com/tecnovert/basicswap/blob/master/doc/install.md)) | 🚧 | ([anon](https://particl.io/)) | - | - | 50% |
|
||||
| [Hinkal](https://hinkal.pro) | - | live | ([Public](https://hinkal.pro/#section-team)) | - | [Competitive security](https://github.com/Secure3Audit/Secure3Academy/blob/main/audit_reports/Hinkal/Hinkal_final_Secure3_Audit_Report.pdf) | 50% |
|
||||
| [Conceal Network](https://conceal.network) | ([GitHub](https://github.com/ConcealNetwork)) | live | ([anon](https://conceal.network/team/)) | [Docs](https://conceal.network/wiki/doku.php) | - | 50% |
|
||||
| [Elusiv](https://elusiv.io) | ([GitHub](https://github.com/elusiv-privacy)) | live | ([Public](https://www.linkedin.com/search/results/people/?currentCompany=%5B%2280778213%22%5D&origin=COMPANY_PAGE_CANNED_SEARCH&sid=s_%40)) | 🚩 **marketing** [Docs](https://docs.elusiv.io/) | - | 50% |
|
||||
| [Fairy](https://fairyswap.finance/swap) | 🚩 **dead** ([GitHub](https://github.com/Fairyswap)) | 🚩 | - | [Docs](https://fairy-swap.gitbook.io/fairyswap-v2/getting-started/about-fairyswap-v2) | 🚩 2022: [Certik](https://skynet.certik.com/projects/fairyswap) | 50% |
|
||||
| [Shade](https://shadeprotocol.io) | ([GitHub](https://github.com/securesecrets/shade)) | live | anon | [Docs](https://docs.shadeprotocol.io/shade-protocol/) | 🚩 2022: [2 audits](https://docs.shadeprotocol.io/shade-protocol/research/audit-log) | 50% |
|
||||
|
||||
**total**: 8 projects
|
||||
|
||||
**Details**:
|
||||
- 3 red flags 🚩
|
||||
|
||||
## 25% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Evanesco](https://evanesco.org) | ([GitHub](https://github.com/Evanesco-Labs)) | live | anon | - | - | 25% |
|
||||
| [BlackBox](https://blackbox.cash) | ([GitHub](https://github.com/TriviumNode)) | 🚧 | anon | - | 25% |
|
||||
| [Spiral Finance](https://www.spiralfi.io) | - | 🚧 | - | ([Docs](https://docs.spiralfi.io/introduction/spiral-finance)) | - | 25% |
|
||||
| [Horizon](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | - | 🚧 | anon | 🚩 **marketing** [Docs](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | [Messier](https://skynet.certik.com/projects/messier) | 25% |
|
||||
| [Umbra](https://app.umbra.cash) | ([GitHub](https://github.com/ScopeLift/umbra-protocol)) | live | anon | - | 🚩 2021: [3 audits](https://app.umbra.cash/faq#security) | 25% |
|
||||
| [Light Shield](https://shield.lightprotocol.com) | - | live | anon | [Docs](https://docs.lightprotocol.com) | 🚩 2022: [Code review](https://github.com/Lightprotocol/light-protocol-v1/blob/main/Audit/Light%20Protocol%20Audit%20Report.pdf) | 25% |
|
||||
| [Sienna Network](https://sienna.network) | 🚩`LOW` ([GitHub](https://github.com/SiennaNetwork)) | 🚧 | anon | [Docs](https://docs.sienna.network/main/) | 🚩 2022: [9 audits](https://sienna.network/audits/) | 25% |
|
||||
|
||||
**total**: 7 projects
|
||||
|
||||
**Details**:
|
||||
- 5 red flags 🚩
|
||||
|
||||
## 0% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Silent protocol](https://www.silentprotocol.org) | - | 🚧 | anon | - | - | 0% |
|
||||
| [Common](https://common.fi) | - | 🚧 | anon | - | - | 0% |
|
||||
| [CIA protocol](https://ciaprotocol.com) | - | 🚧 | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [CoinBook](https://www.coinbook.app) | - | 🚧 | anon | - | - | 0% |
|
||||
| [Seven Seas](https://www.sevenseas.exchange) | - | 🚧 | - | - | - | - | 0% |
|
||||
| [NonKYC](https://nonkyc.io) | - | 🚧 | - | - | - | - | 0% |
|
||||
| 🚩 **sunset** [zk.money](https://zk.money) | ([Docs](https://docs.aztec.network/zk-money/userguide)) | 🚩 | anon | [Docs](https://docs.aztec.network) | - | 0% |
|
||||
| 🚩 **sunset** [Yellow Submarine](https://ys.finance) | ([Docs](https://yellow-s.gitbook.io/docs/ys-basics/introduction)) | 🚧 | anon | - | - | 0% |
|
||||
| [Sacred](https://sacred.finance) | 🚩 **LOW** ([GitHub](https://github.com/Sacred-Finance)) | 🚧 | anon | - | - | 0% |
|
||||
| [StealthPay](https://www.stealthpay.cash) | 🚩 **dead** ([GitHub](https://github.com/cryptoadong)) | 🚧 | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [XATA](https://www.xata.fi) | - | 🚩 | anon | ([Docs](https://docs.xata.fi)) | - | 0% |
|
||||
| [Offshift](https://www.offshift.io) | 🚩 **LOW** ([GitLab](https://open.offshift.io/offshiftXFT)) | live | ([anon](https://offshift.io/#team)) | - | - | 0% |
|
||||
| [zkUSD](https://zkusd.money/#Features) | 🚩 **no code** ([GitHub](https://github.com/zkUSDLabs)) | 🚧 | - | 🚩 **marketing** [Docs](https://zkusd.gitbook.io/zkusd-documentation) | - | 0% |
|
||||
| [Shade Cash](https://shade.cash) | 🚩 **no code** ([GitHub](https://github.com/ShadeCash)) | 🚧 | - | 🚩 **marketing** [Docs](https://shadecash.gitbook.io/shadecash) | - | 0% |
|
||||
| 🚩 **sunset** [Sahara](https://sahara.network) | - | 🚩 | ([Public](https://sahara.network/)) | - | 🚩 2022: [Vesting contract](https://sahara.network/resources/sahara-security-audit.pdf) | 0% |
|
||||
| [Hurricane Protocol](https://hurricane.money) | 🚩 **no code** ([GitHub](https://github.com/Hurricane-Protocol)) | 🚩 | anon | 🚩 **marketing** [Docs](https://docs.hurricane.money) | - | 0% |
|
||||
| 🚩 **sunset** [DeFiner](https://definer.org) | ([GitHub](https://github.com/DeFinerOrg)) | 🚩 | anon | [Docs](https://docs.definer.org) | 🚩 2020: [Savings audits](https://docs.definer.org/v/copy-of-definer.org/security/audits) | 75% |
|
||||
|
||||
**total**: 17 projects
|
||||
|
||||
**Details**:
|
||||
- 17 red flags 🚩
|
||||
- 6 sunsets
|
||||
|
||||
# 🚧-flag applicable breakdown (exclusion criteria)
|
||||
|
||||
**Note**:
|
||||
- 🚧 - represents that the project is not live on mainnet, this is an exclusion criteria that forces project score to be 0%
|
||||
|
||||
## 100% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [RAILGUN](https://railgun.org) | [Github](https://github.com/Railgun-Community) | live | ([Public](https://railgun.org/#/contributors)) | [Docs](https://docs.railgun.org/developer-guide/cookbook/cookbook-overview) | [5 audits](https://assets.railgun.org/docs/audits/) | 100% |
|
||||
|
||||
**total**: 1 project
|
||||
|
||||
## 75% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- | ------------ | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Firn Protocol](https://app.firn.cash) | ([GitHub](https://github.com/firnprotocol)) | live | anon | [Docs](https://docs.firn.cash) | [BlockSec](https://github.com/blocksecteam/audit-reports/blob/main/solidity/blocksec_firnprotocol_v1.0-signed.pdf) | 75% |
|
||||
|
||||
**total**: 1 projects
|
||||
|
||||
**Details**:
|
||||
- 1 red flag 🚩
|
||||
|
||||
## 50% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Hinkal](https://hinkal.pro) | - | live | ([Public](https://hinkal.pro/#section-team)) | - | [Competitive security](https://github.com/Secure3Audit/Secure3Academy/blob/main/audit_reports/Hinkal/Hinkal_final_Secure3_Audit_Report.pdf) | 50% |
|
||||
| [Conceal Network](https://conceal.network) | ([GitHub](https://github.com/ConcealNetwork)) | live | ([anon](https://conceal.network/team/)) | [Docs](https://conceal.network/wiki/doku.php) | - | 50% |
|
||||
| [Elusiv](https://elusiv.io) | ([GitHub](https://github.com/elusiv-privacy)) | live | ([Public](https://www.linkedin.com/search/results/people/?currentCompany=%5B%2280778213%22%5D&origin=COMPANY_PAGE_CANNED_SEARCH&sid=s_%40)) | 🚩 **marketing** [Docs](https://docs.elusiv.io/) | - | 50% |
|
||||
| [Fairy](https://fairyswap.finance/swap) | 🚩 **dead** ([GitHub](https://github.com/Fairyswap)) | 🚩 | - | [Docs](https://fairy-swap.gitbook.io/fairyswap-v2/getting-started/about-fairyswap-v2) | 🚩 2022: [Certik](https://skynet.certik.com/projects/fairyswap) | 50% |
|
||||
| [Shade](https://shadeprotocol.io) | ([GitHub](https://github.com/securesecrets/shade)) | live | anon | [Docs](https://docs.shadeprotocol.io/shade-protocol/) | 🚩 2022: [2 audits](https://docs.shadeprotocol.io/shade-protocol/research/audit-log) | 50% |
|
||||
|
||||
**total**: 5 projects
|
||||
|
||||
**Details**:
|
||||
- 5 red flags 🚩
|
||||
|
||||
## 25% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Evanesco](https://evanesco.org) | ([GitHub](https://github.com/Evanesco-Labs)) | live | anon | - | - | 25% |
|
||||
| [Umbra](https://app.umbra.cash) | ([GitHub](https://github.com/ScopeLift/umbra-protocol)) | live | anon | - | 🚩 2021: [3 audits](https://app.umbra.cash/faq#security) | 25% |
|
||||
| [Light Shield](https://shield.lightprotocol.com) | - | mlive | anon | [Docs](https://docs.lightprotocol.com) | 🚩 2022: [Code review](https://github.com/Lightprotocol/light-protocol-v1/blob/main/Audit/Light%20Protocol%20Audit%20Report.pdf) | 25% |
|
||||
|
||||
**total**: 3 projects
|
||||
|
||||
**Details**:
|
||||
- 2 red flags 🚩
|
||||
|
||||
## 0% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Manta Pay](https://app.manta.network/dolphin/transact) | ([GitHub](https://github.com/Manta-Network)) | 🚧 | public | [Docs](https://docs.manta.network/docs/Introduction) | - | 0% |
|
||||
| [Webb](https://app.webb.tools/#/tornado) | ([GitHub](https://github.com/webb-tools)) | 🚧 | anon | [Docs](https://docs.webb.tools/docs/) | [Audit of the DKG-Substrate pallet](https://blog.webb.tools/webbs-evm-bridge-security-audit-completed-by-veridise/) | 0% |
|
||||
| [Diva](https://www.diva.exchange/en/) | ([GitHub](https://github.com/diva-exchange)) | 🚧 | ([Public](https://www.diva.exchange/en/team-and-contact/)) | [Docs](https://docs.lightprotocol.com) | - | - | 0% |
|
||||
| [CAPE](https://www.espressosys.com/product) | ([GitHub](https://github.com/EspressoSystems/cape)) | 🚧 | anon | [Docs](https://docs.espressosys.com/sequencer/espresso-sequencer-architecture/readme) | - | 0% |
|
||||
| [Dusk Network](https://dusk.network) | ([GitHub](https://github.com/dusk-network)) | 🚧 | ([Public](https://dusk.network/pages/team)) | - | - | 0% |
|
||||
| [BasicSwap](https://basicswapdex.com) | ([GitHub](https://github.com/tecnovert/basicswap/blob/master/doc/install.md)) | 🚧 | ([anon](https://particl.io/)) | - | - | 0% |
|
||||
| [BlackBox](https://blackbox.cash) | ([GitHub](https://github.com/TriviumNode)) | 🚧 | anon | - | 0% |
|
||||
| [Spiral Finance](https://www.spiralfi.io) | - | 🚧 | - | ([Docs](https://docs.spiralfi.io/introduction/spiral-finance)) | - | 0% |
|
||||
| [Horizon](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | - | 🚧 | anon | 🚩 **marketing** [Docs](https://messier.gitbook.io/catalogue-de-messier/messier-applications/horizon) | [Messier](https://skynet.certik.com/projects/messier) | 0% |
|
||||
| [Sienna Network](https://sienna.network) | 🚩`LOW` ([GitHub](https://github.com/SiennaNetwork)) | 🚧 | anon | [Docs](https://docs.sienna.network/main/) | 🚩 2022: [9 audits](https://sienna.network/audits/) | 0% |
|
||||
| [Silent protocol](https://www.silentprotocol.org) | - | 🚧 | anon | - | - | 0% |
|
||||
| [Common](https://common.fi) | - | 🚧 | anon | - | - | 0% |
|
||||
| [CIA protocol](https://ciaprotocol.com) | - | 🚧 | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [CoinBook](https://www.coinbook.app) | - | 🚧 | anon | - | - | 0% |
|
||||
| [Seven Seas](https://www.sevenseas.exchange) | - | 🚧 | - | - | - | - | 0% |
|
||||
| [NonKYC](https://nonkyc.io) | - | 🚧 | - | - | - | - | 0% |
|
||||
| [zkUSD](https://zkusd.money/#Features) | 🚩 **no code** ([GitHub](https://github.com/zkUSDLabs)) | 🚧 | - | 🚩 **marketing** [Docs](https://zkusd.gitbook.io/zkusd-documentation) | - | 0% |
|
||||
| [Shade Cash](https://shade.cash) | 🚩 **no code** ([GitHub](https://github.com/ShadeCash)) | 🚧 | - | 🚩 **marketing** [Docs](https://shadecash.gitbook.io/shadecash) | - | 0% |
|
||||
| 🚩 **sunset** [zk.money](https://zk.money) | ([Docs](https://docs.aztec.network/zk-money/userguide)) | 🚩 | anon | [Docs](https://docs.aztec.network) | - | 0% |
|
||||
| 🚩 **sunset** [Yellow Submarine](https://ys.finance) | ([Docs](https://yellow-s.gitbook.io/docs/ys-basics/introduction)) | TBD | anon | - | - | 0% |
|
||||
| [Sacred](https://sacred.finance) | 🚩 **LOW** ([GitHub](https://github.com/Sacred-Finance)) | TBD | anon | - | - | 0% |
|
||||
| [StealthPay](https://www.stealthpay.cash) | 🚩 **dead** ([GitHub](https://github.com/cryptoadong)) | TBD | anon | - | - | 0% |
|
||||
| 🚩 **sunset** [XATA](https://www.xata.fi) | - | 🚩 | anon | ([Docs](https://docs.xata.fi)) | - | 0% |
|
||||
| [Offshift](https://www.offshift.io) | 🚩 **LOW** ([GitLab](https://open.offshift.io/offshiftXFT)) | live | ([anon](https://offshift.io/#team)) | - | - | 0% |
|
||||
| 🚩 **sunset** [Sahara](https://sahara.network) | - | 🚩 | ([Public](https://sahara.network/)) | - | 🚩 2022: [Vesting contract](https://sahara.network/resources/sahara-security-audit.pdf) | 0% |
|
||||
| [Hurricane Protocol](https://hurricane.money) | 🚩 **no code** ([GitHub](https://github.com/Hurricane-Protocol)) | 🚩 | anon | 🚩 **marketing** [Docs](https://docs.hurricane.money) | - | 0% |
|
||||
| 🚩 **sunset** [DeFiner](https://definer.org) | ([GitHub](https://github.com/DeFinerOrg)) | 🚩 | anon | [Docs](https://docs.definer.org) | 🚩 2020: [Savings audits](https://docs.definer.org/v/copy-of-definer.org/security/audits) | 0% |
|
||||
| [Panther Protocol](https://www.pantherprotocol.io) | ([GitHub](https://github.com/pantherprotocol)) | [testnet](https://docs.pantherprotocol.io/docs/product-and-technological-components/product-versions/v1-testnet) | ([Public](https://www.pantherprotocol.io/)) | [Docs](https://docs.pantherprotocol.io/docs/start-here/panther-protocol-documentation) | 🚩 2021: [ZKP Vesting](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Vesting.pdf), [ZKP Token](https://www.pantherprotocol.io/resources/REP-Panther-ZKP-Token.pdf) | 75% |
|
||||
|
||||
**total**: 27 projects
|
||||
|
||||
**Details**:
|
||||
- 17 🚧
|
||||
- 25 red flags 🚩
|
||||
- 6 sunsets
|
||||
|
||||
# Findings
|
||||
|
||||
## DeFi category
|
||||
|
||||
1. 38 projects
|
||||
2. 25 🚩red flags
|
||||
3. 17 🚧
|
||||
4. 6 sunsets
|
||||
|
||||
**Before 🚧 criteria has been applied**
|
||||
|
||||
_high-risk category_
|
||||
- 44.7% of the projects scored 0%
|
||||
- 18.4% scored 25%
|
||||
- 63.1% of the total projects - high-risk category (0-25%)
|
||||
|
||||
_low-risk category_
|
||||
- 2.6% of the projects hit 100%
|
||||
- 13.1% hit 75%
|
||||
- 14.1% combined - low-risk category
|
||||
|
||||
_moderate risk-category_
|
||||
- 21% - moderate risk-category
|
||||
|
||||
**GitHub**
|
||||
- 27 projects (71%) have public GitHub
|
||||
- 8 projects (29% among them) have dead or inactive GitHub (6 months +)
|
||||
|
||||
**security audits**
|
||||
- 13 projects or 34.2% have third-party audits
|
||||
- 8 projects have outdated audits (1 year+) - 61% (among those attested by a third party)
|
||||
|
||||
**docs**
|
||||
- 21 projects (or 55%) have docs
|
||||
- 5 projects (or 23%) among them = marketing docs
|
||||
|
||||
**After 🚧 criteria has been applied**
|
||||
- 44.7% - 🚧
|
||||
- 71% - 0%
|
||||
- 13.1% - 50%
|
||||
- 7.8% - 25%
|
||||
- 5.2% - 75%
|
||||
|
||||
**Basic assessment, 🚩& 🚧 criterias applicability comparison**
|
||||
|
||||
| Observation | Basic | 🚩 | 🚧 |
|
||||
| ------------- | ------------- | ------------- | ------------- |
|
||||
| 100% | 5.2% | 2.6% | 2.6% |
|
||||
| 75% | 23.6% | 13.1% | 5.2% |
|
||||
| 50% | 31.5% | 21% | 13.1% |
|
||||
| 25% | 23.6% | 18.4% | 7.8% |
|
||||
| 0 | 15.7% | 44.7% | 71% |
|
||||
65
Web3privacynowplatform/scoringmodel/Framework_update.md
Normal file
|
|
@ -0,0 +1,65 @@
|
|||
# Scoring model Framework update
|
||||
|
||||
[Applied scoring approach](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/E9QPx9iKgPXPqEsAN-YklipSRJy9VTBMOLwwEcqqVpU)
|
||||
|
||||
**MVP**
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test project** | available & active GitHub / not (25%) | Live or 🚧 (exclusion criteria) | public team / not (25%) | available & not marketing docs / not (25%) | available & up to date third-party audit / not (25%) | total |
|
||||
| **score** | 25% | 🚧 | 25% | 25% | 25% | from 0% to 100% |
|
||||
|
||||
**MVP with personal information concern**
|
||||
| Project | GitHub | Product-readiness | Personal information | Team | Docs | Audit | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test project** | available & contentful & active GitHub / not (20%) | Live or 🚧 (exclusion criteria) | personal information hidden & not (20%) | public team / not (20%) | available & techno-instructive docs / not (20%) | available & up to date third-party audit / not (20%) | total |
|
||||
| **score** | 20% | 🚧 | 20% | 20% | 20% | 20% | from 0% to 100% |
|
||||
|
||||
**Extended**
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Contributors | Licenses | Support | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test project** | available & active GitHub / not (25%) | Live or 🚧 (exclusion criteria) | public team / not (25%) | available & not marketing docs / not (25%) | available & up to date third-party audit / not (25%) | external contributors outside of the team members | What licenses are in use | Some form of support available? (telegram, discord, forum) | from 0 to 100% |
|
||||
| **score** | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 100% |
|
||||
|
||||
**How to use**
|
||||
| Project | GitHub | Product-readiness | Personal information | Team | Docs | Audit | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test Project** | 1. Exist. 2. Active (last 6 months). 3. Continuous commits. 4. Containing codes and scripts. | 1. Live project (main-net, Beta). 2. Accessible app or user interface. | 1. Anonymous account handler. 2. Real IP hidden. | Public team | 1. Exist. 2. Dev-centric and instructive. | 1. Exist. 2. Up to date (last 6 months). 3. Complex.
|
||||
| **score** | 20% | 🚧 | 20% | 20% | 20% | 20% | from 0% to 100% |
|
||||
|
||||
**How to use (Extended)**
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Contributors | Licenses | Support | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test project** | 1. Exist. 2. Active (last 6 months). 3. Lots of commits (not fake). | 1. Live (main-net, Beta). | Public team | 1. Exist. 2. Dev-centric. | 1. Exist. 2. Up to date (last 6 months). 3. Complex. | External contributors | Open-source licenses in use | Availbale | from 0 to 100% |
|
||||
| **score** | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 100% |
|
||||
|
||||
## **Red flag examples**
|
||||
|
||||
# **Poor GitHub**
|
||||
🚩
|
||||
.png?raw=true)
|
||||
|
||||
# **Personal information required for enabling account**
|
||||
.png?raw=true)
|
||||
|
||||
# **Outdated Audit**
|
||||
🚩_check_: date; _result_: outdated (1 year+)
|
||||
.png?raw=true)
|
||||
|
||||
# **Marketing docs**
|
||||
🚩_check_: language (verbal & visual), if it's for developers & how complex (# of pages) it is; _result_: marketing - non-technical
|
||||
.png?raw=true)
|
||||
|
||||
.png?raw=true)
|
||||
|
||||
# **Sunset**
|
||||
🚩_check_: the last updates; _result_: inactive since 2021
|
||||
.png?raw=true)
|
||||
|
||||
.png?raw=true)
|
||||
|
||||
# **Team**
|
||||
🚩_check_: public team; _result_: anon
|
||||
.png?raw=true)
|
||||
|
||||
# **Summary**
|
||||

|
||||
|
|
@ -0,0 +1,40 @@
|
|||
# A new scheme of scoring model
|
||||
|
||||
| Criteria | Detail | Validity level | Score |
|
||||
| ---------------- | ------------------------ | ---------------------- | ------ |
|
||||
| Referrable source code | Available git repo and doc, and the functionality presented in the doc is referred in the git repo | No repo or doc (0), not referrable repo with doc (1), referrable repo with doc (2) | 50-Δ% |
|
||||
| Audit | Open to audit and up-to-date third-party audit | Not open to audit(0), open to audit without up-to-date third-party audit (1), up-to-date third-party audit (2) | 25% |
|
||||
| Anonymity | Registration and connection does not depend on user's real identity | Real identity required (0), linkable identity required (1), full anonymous (2) | 25% |
|
||||
| Decentralization | Decentralized storage and administration | Not fully decentralized (0), fully decentralized (1) | Δ% |
|
||||
|
||||
## Explanation of the criteria
|
||||
|
||||
**Referrable source code**
|
||||
- For non-techies
|
||||
- Check the existence of public git repository and doc
|
||||
- Check the existence of code files in the git repository
|
||||
- List the focusing privacy-preserving points in the doc
|
||||
- Check the reference of code file names with the focusing points
|
||||
- For beginner techies:
|
||||
- Check the existence of public git repository and doc
|
||||
- Check the existence of code files in the git repository and view the code
|
||||
- List the privacy-preserving measures in the doc and seek the reference in the source code
|
||||
|
||||
**Audit**
|
||||
- For non-techies and beginner techies
|
||||
- Check the existence of an application or other type of implementation of the project and its availability towards third-party audits
|
||||
- Check the audit history of the project
|
||||
|
||||
**Anonymity**
|
||||
- For non-techies:
|
||||
- Register an account or use personal account of other on-chain project to connect to the network or launch the app
|
||||
- List the information required for the account
|
||||
- For beginner techies:
|
||||
- The task as non-techies
|
||||
- Also with the presence of IP-obfuscation techniques (Tor, etc.) in the project
|
||||
|
||||
**Decentralization**
|
||||
- For non-techies and beginner techies:
|
||||
- Check the power distribution of management in the doc (if pointed);
|
||||
- Check the information about server location (if exists);
|
||||
|
||||
|
|
@ -0,0 +1,89 @@
|
|||
# Product features
|
||||
|
||||
Here we prototype potential product features within our "l2beat for privacy" platform. All they are based on market survey available [here]((https://docs.google.com/spreadsheets/d/1JWpAsGL10UTsVeuIVbouzUxRjaSPUAamxcbFljXuUWE/edit?usp=sharing))
|
||||
|
||||
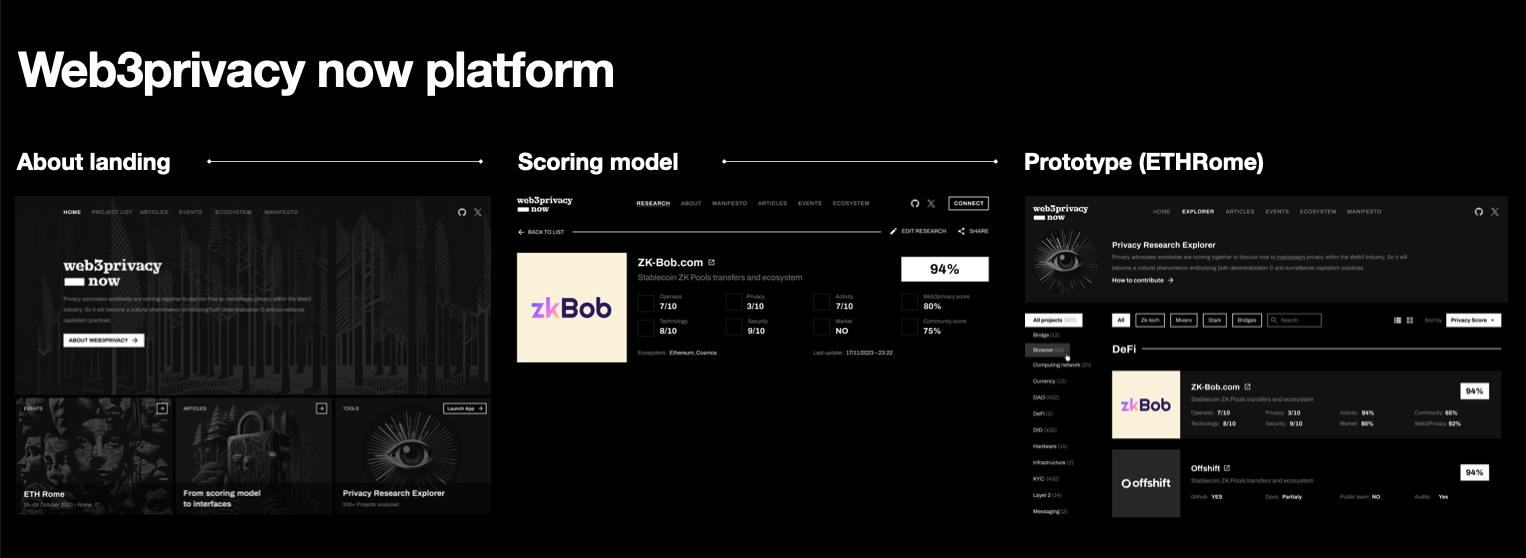
|
||||
|
||||
# Validity track
|
||||
|
||||
"yes/no" applicability like if "docs" exist or not.
|
||||
_Benefit_: easy to source manually & empower scoring model with the links.
|
||||
_Downside_: the existence of Git repo or docs doesn't guarantee the state of privacy within a certain solution.
|
||||
|
||||
**Approach**: "validity track" serves as an MVP of privacy analytics, and challenges a culture of open-source delivery.
|
||||
|
||||
_Validity examples_ (yes, no):
|
||||
- Github repo
|
||||
- Docs
|
||||
- Public team
|
||||
- Third-party audit
|
||||
|
||||
This could be broken down into 100% (4 yes, each - 25%; where 2 no & 2 yes = 50%)
|
||||
|
||||
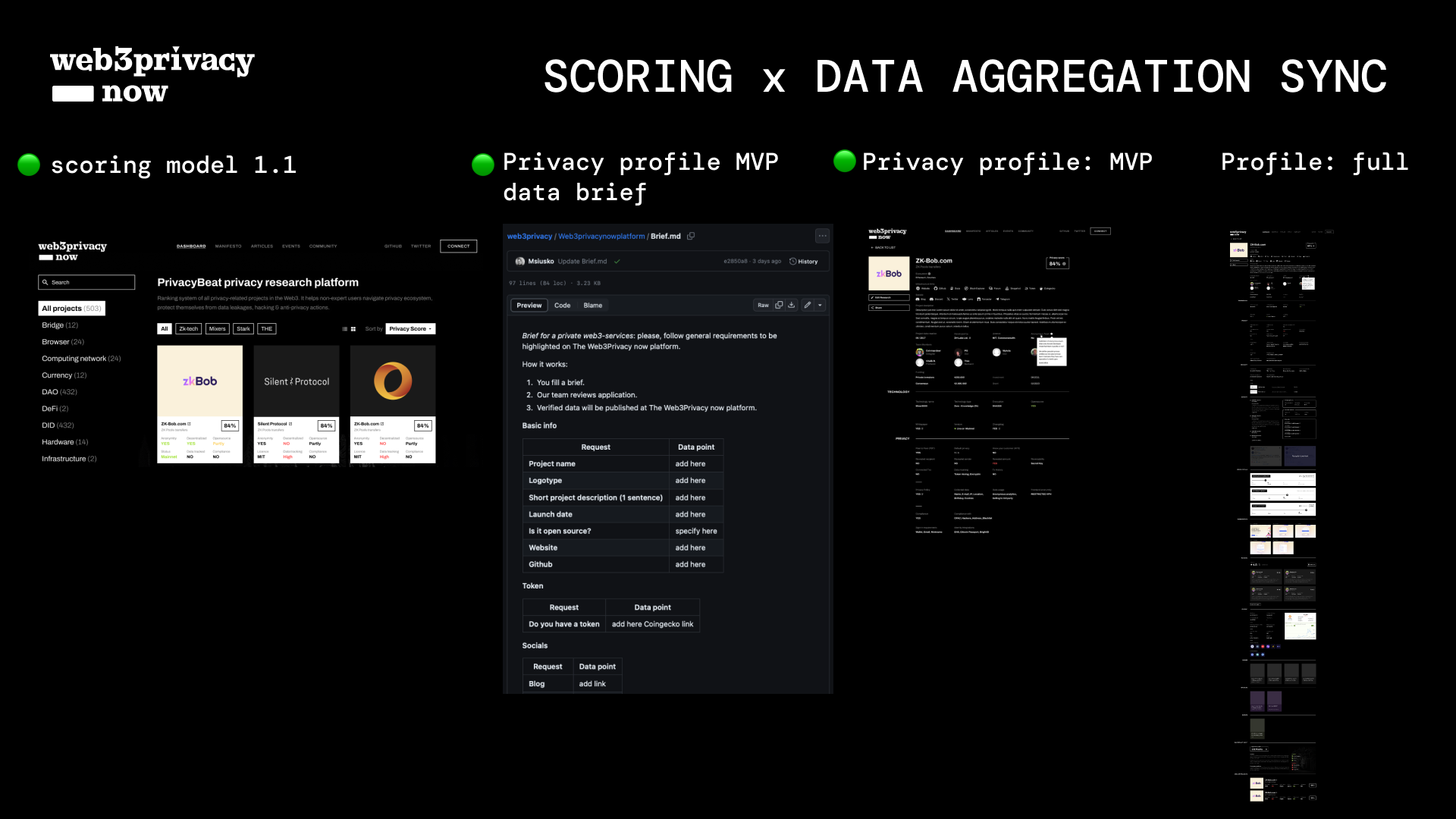
|
||||
|
||||
## 101 educational materials.
|
||||
|
||||
| _Benefit_ | _Downside_ | **Approach** | _Selected 101s_ |
|
||||
| ------------- | ------------- | ------------- | ------------- |
|
||||
| significantly upgrades DYOR & flags main misconceptions about privacy execution plus 1 guide could serve all audiences | too many content pieces to write or assemble to encompass the whole privacy services & nuances spectrum (needed to be broken down into delivery phases) | select essential educational materials for the first audiences (example: crypto, but not privacy native instead of "non-crypto" first served) | privacy tech vocabulary |
|
||||
| | | make 101 modular (block system) + composable (to be reused in other guides) | privacy data leakages 101 |
|
||||
| | | | transaction traceability 101 (the basics on Etherscan example) |
|
||||
| | | | web3 comms 101 (with a focus on misleading comms that create an obscure understanding of the tech/product) |
|
||||
|
||||
The scoring model could consist of passive & active parts. When passive means what could be automated or req no subjective gaze, active - for personal consideration (research).
|
||||
|
||||
## Checklists (example: trusted sources list).
|
||||
|
||||
| _Benefit_ | _Downside_ | **Approach** | _Checklist MVP_ |
|
||||
| ------------- | ------------- | ------------- | ------------- |
|
||||
| serves as a self-check navigation within the complex audit stream (and a predecessor of an actionable database) | there will be always something missing from the list | pick a direction (like "trusted sources") | **Storage**: What user information is stored? (username, IP address, last connection, wallets associate, etc) -> the less the better |
|
||||
| | | write down it as an actionable plan | **Infra**: Number of nodes/servers/ -> the larger the footprint the best privacy |
|
||||
| | | help a person spend less time on data aggregation (the easiest to follow checklist - the better) | **Signup**: no email or tel number for signup -> the less data the better |
|
||||
| | | | **Traction**: number of people using it -> the more the better (with examples) |
|
||||
| | | | **Public comms**: simplified socials analysis (for a negative sentiment) |
|
||||
| | | | **Product-readiness**: test-net, mainnet; date of the release. |
|
||||
|
||||
This is a mix of objective metrics & subjective takeaways (like an old product release can be a negative sentiment for privacy & vice versa). Case studies will help to empower these assumptions.
|
||||
If we will collect good case studies lib -> it will help people to have market benchmarks for every step of scoring system.
|
||||
|
||||
# Academy (content from case studies to third-party services to check net data, leakages).
|
||||
|
||||
| _Benefit_ | _Downside_ | **Approach** |
|
||||
| ------------- | ------------- | ------------- |
|
||||
| this will be the backbone of our platform in the future that will bridge the gap between lack of privacy-centric education, lack of third-party services to check-up solutions & poor transparency on behalf of privacy-devs. | usually takes too long time to deliver & many different contributors (should be simplified via tracks like Web3 Privacy 101). | Stick with privacy 101 (basics). |
|
||||
| | | Brake down the most crucial knowledge into simplified blocks. |
|
||||
| | | Create a simplified & actionable "lecture framework" for guest lectors. |
|
||||
| | | Invite lectors within a micro-learning format. |
|
||||
| | | Cover basic 10 lectures via "Web3 privacy 101 introduction". |
|
||||
| | | Deploy via videos + texts > test them out. |
|
||||
|
||||
## _Long 2do list (filtered out product features)_
|
||||
|
||||
| **Validity** | **Education track 101** | **Checklists** | **Additional content** | **Automation (beta)** |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| * documentation: exists/missing | forkability x privacy 101 | trusted sources checklist (&/or a list) | case studies when solutions actively embed privacy education within the workflow | "DERP"-alike tool for the future privacy script-based "check-up" product releases |
|
||||
| 3rd party list (yes/no) from security audit agencies to independent security engineers (+their reputation 101 in later versions) | security audits 101 (basics) | web3 open-source checklist (soft screening like whitepaper (yes/no), docs (yes/no) etc) | List of external third-party resources in a Wiki (for those, who like to make extra effort -> influence micro-services creation) | web3-native IP-checker for a beta version |
|
||||
| website checklist (1-2-3-4-5..., yes/no validity) | web3 privacy 101 (focus on a misleading comms like blockchain security equals privacy) | different self-check recommendations by security audits, white hackers as a supplement (how would you test product privacy) | case-studies (privacy matching): protocol = transparent, but use-cases = private (like Ethereum) | web3-native privacy features checker to be R&D (what could be automated & coded for QA-automation) |
|
||||
| code audit (yes/no). Case studies (how those audits could look alike with active links) | web3 comms 101 (with a focus on misleading comms that create an obscure understanding of the tech/product) | GitHub basic score (flag system could be a part of the second product release) | future: privacy features comparison within solutions (creating a comprehensive privacy market metrics set) ||
|
||||
| | privacy tech vocabulary | a checklist of when you need a "tech" person help to attest privacy features & when not (with a focus on a second scenario) | case studies when solutions actively embed privacy education within the workflow ||
|
||||
| | privacy data leakages 101 | | "net usage stats" services guide for the end user (but with a focus on empowering product managers to incorporate third-party tools to self-check their products & publicly report on their privacy features) | |
|
||||
| | transaction traceability 101 (the basics on Etherscan example) | | "privacy stack" enhancement prototyping (1 solution + 1 solution = privacy "2x" (like Session messenger + dVPN) ||
|
||||
| | web3 comms 101 (with a focus on misleading comms that create an obscure understanding of the tech/product) | | examples of how products enhance privacy creatively (like a game mentioned by Obscuro) -> potential market benchmarks ||
|
||||
| | open source 101 (short version) | | part of the wiki: web3 privacy products biases (in relation to privacy features x user experience) ||
|
||||
| | social recovery 101 | ||
|
||||
| | missing 3rd party audit potential risks 101 | ||
|
||||
| | simplified media analysis 101 | ||
|
||||
| | privacy in ZK 101 | ||
|
||||
| | "attacks" (threats) 101 | ||
|
||||
| | transaction traceability 101 (the basics on Etherscan example) | ||
|
||||
| | web3 docs 101 (basic description in relation to privacy) | ||
|
||||
| | pubkey, network key, viewing key etc 101 | ||
|
||||
| | "Anti-features" 101 | ||
|
||||
| | did 101 (with a focus on the linkage between different data types) | ||
|
||||
|
||||
## _DYOR section_
|
||||
* useful links (like dVPN studies in a DYOR section)
|
||||
|
||||
## _Future releases_
|
||||
* in the future: collab with a security audit company to create a new docs audit service description when a third party will attest privacy features of the initial idea x tooling description
|
||||
40
Web3privacynowplatform/scoringmodel/Readme.md
Normal file
|
|
@ -0,0 +1,40 @@
|
|||
# Scoring model analytics based on a 50+ privacy projects [survey](https://docs.google.com/spreadsheets/d/1JWpAsGL10UTsVeuIVbouzUxRjaSPUAamxcbFljXuUWE/edit?usp=sharing)
|
||||
|
||||
_We are shipping an educational website to help the general public understand whether a web3-service is private or not. Its core feature - scoring mechanism validated by the market (reference: web3 - l2beat, web2 - IMDB)._
|
||||
|
||||
| Original idea | Privacy market survey | Scoring model MVP | Community feedback model 1.1 | ETHRome data set | DeFi category scoring x model 1.2 | Playbook for non-techies 1.3 |
|
||||
| ------------- | ------------- |------------- |------------- | ------------- | ------------- | ------------- |
|
||||
| [link](https://github.com/web3privacy/web3privacy/tree/main/Web3privacynowplatform) | [link](https://github.com/web3privacy/web3privacy/tree/main/Web3privacynowplatform/scoringmodel/Survey) | [link](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Web3Privacy%20Now%20scoring%20platform_test%20framework.pdf) | [link](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/E9QPx9iKgPXPqEsAN-YklipSRJy9VTBMOLwwEcqqVpU) | [link](https://taikai.network/ethrome/hackathons/ethrome-23/projects/clng508ts00lswu01030hpfuq/idea) | [link](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/DeFi%20category%20prototype.md) | [link](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/90XEXa7AG_qc-VgYKs40i88xB1HF97gr1zqb-qvnif0) |
|
||||
|
||||
**17 Oct, 2023 update**
|
||||
|
||||
**2 DO list**
|
||||
|
||||
_Analyze_
|
||||
- Analyze latest privacy scoring assessment [here](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/E9QPx9iKgPXPqEsAN-YklipSRJy9VTBMOLwwEcqqVpU)
|
||||
- Analyze [Data manifesto made during ETHRome](https://github.com/web3privacy/data/tree/main#readme)
|
||||
- Analyze pull requests by Railgun, Waku, Lit, Discreet, Webb [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/Brief.md)
|
||||
|
||||
_Create_
|
||||
- Github page in this [repo](https://github.com/web3privacy/web3privacy/tree/main/Web3privacynowplatform/scoringmodel)
|
||||
- Enrich scoring model MVP with the new parameters that could be easily automated or quickly manually aggregated (if not - move data set into a backlog)
|
||||
- Try to apply previous scoring model approach (with % &/or semaphore take: green, yellow, red) to new parameters & observe how scoring model could change (write down potential changes & implications)
|
||||
|
||||
_Delivery_
|
||||
- Final page will be breaken down into:
|
||||
- Updated scoring model MVP data set (without scoring approach)
|
||||
- Simulation of the old MVP + new MVP: how scoring could change with new parameters
|
||||
- Backlog (data that can't be quickly parsed)
|
||||
|
||||
# Backlog
|
||||
|
||||
- MVP description: [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Web3Privacy%20Now%20scoring%20platform_test%20framework.pdf)
|
||||
- Initial idea: [here](https://github.com/web3privacy/web3privacy/tree/main/Web3privacynowplatform)
|
||||
- [Privacy players' survey](https://github.com/web3privacy/web3privacy/tree/main/Web3privacynowplatform/scoringmodel/Survey)
|
||||
- Test framework: [PDF](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Web3Privacy%20Now%20scoring%20platform_test%20framework.pdf)
|
||||
- Latest scoring assessment: [here](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/E9QPx9iKgPXPqEsAN-YklipSRJy9VTBMOLwwEcqqVpU)
|
||||
- [ETHRome prototype](https://taikai.network/ethrome/hackathons/ethrome-23/projects/clng508ts00lswu01030hpfuq/idea)
|
||||
- [DeFi category testing](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/DeFi%20category%20prototype.md)
|
||||
- [Scoring assessment 1.0 explainer](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Framework_update.md)
|
||||
- [Data brief x 1.0 comparison](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/Data%20brief%20%26%20scoring%20model%20comparison.md)
|
||||
- [Platform features backlog](https://github.com/web3privacy/web3privacy/tree/main/Web3privacynowplatform/scoringmodel/Product%20features)
|
||||
|
|
@ -0,0 +1,86 @@
|
|||
# Community feedback x our Scoring model 1.2 version.
|
||||
|
||||
**Main goal**: to have an MVP on how non-techies could analyze if the project is private or not (think of "IMDB" or "L2beat" for privacy)
|
||||
|
||||
**Sub-goal**: to have a more objective scoring model made in collaboration with the privacy community.
|
||||
|
||||
**Context**:
|
||||
- _Persona_: a web3 casual user without dev knowledge & privacy illiterate. He/she/they has limited time for research & needs to perform simple steps to ensure that service is private.
|
||||
- _Assessment categories_: we broke down analytics flow into 2 main categories: validity track (quick check-up) & DYOR (do your own research that requires more time & subjective opinion).
|
||||
|
||||
# Sandbox: DeFi category that has been analyzed
|
||||
|
||||
**How to use sandbox?**
|
||||
1. Read takeaways.
|
||||
2. Give us feedback via general comments in the Community on [Signal](https://chat.web3privacy.info/) or make a Pull request here.
|
||||
3. You can always explore 38 DeFi project' assessment [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/DeFi%20category%20prototype.md)
|
||||
|
||||
# Scoring model 1.2: validity track
|
||||
|
||||
_Validity track covers GitHub, Product-readiness, Team, Docs, Audit._
|
||||
|
||||
**Note**: quick assessment helps to decrease privacy dark patterns from obscure language to test-net claiming it has a "state of art privacy".
|
||||
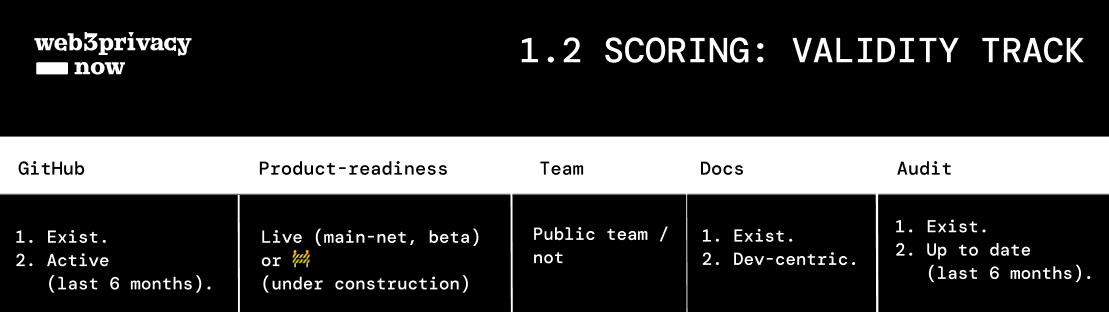
|
||||
|
||||
We use % as a simplified way to prototype scoring model (from % to 100%). Later versions will include a mixmodel of %, yes/no assumptions & much complex observations.
|
||||

|
||||
|
||||
# Practical examples
|
||||
## 100% scoring
|
||||
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [RAILGUN](https://railgun.org) | [Github](https://github.com/Railgun-Community) | live | ([Public](https://railgun.org/#/contributors)) | [Docs](https://docs.railgun.org/developer-guide/cookbook/cookbook-overview) | [5 audits](https://assets.railgun.org/docs/audits/) | 100% |
|
||||
|
||||
## 0% scoring
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Score |
|
||||
| ------------- |------------- |------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| [Sienna Network](https://sienna.network) | 🚩`LOW` ([GitHub](https://github.com/SiennaNetwork)) | 🚧 | anon | [Docs](https://docs.sienna.network/main/) | 🚩 2022: [9 audits](https://sienna.network/audits/) | 0% |
|
||||
| [Silent protocol](https://www.silentprotocol.org) | - | 🚧 | anon | - | - | 0% |
|
||||
| [Common](https://common.fi) | - | 🚧 | anon | - | - | 0% |
|
||||
| [CIA protocol](https://ciaprotocol.com) | - | 🚧 | anon | - | - | 0% |
|
||||
|
||||
38 projects from the privacy x DeFi category were scored [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/DeFi%20category%20prototype.md)
|
||||
|
||||
# **Red flag examples**
|
||||
|
||||
## **Poor GitHub**
|
||||
.png?raw=true)
|
||||
|
||||
https://github.com/Hurricane-Protocol
|
||||
|
||||
## **Outdated Audit**
|
||||
🚩check: date; _result_: outdated (1 year+)
|
||||
.png?raw=true)
|
||||
https://docs.definer.org/v/copy-of-definer.org/security/audits
|
||||
|
||||
## **Marketing docs**
|
||||
🚩check: language (verbal & visual), if it's for developers & how complex (# of pages) it is; _result_: marketing - non-technical
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/staticobjects/Marketing%20docs%20(ShadeCash).png" width="600"/>
|
||||
|
||||
https://shadecash.gitbook.io/shadecash/token/token-and-distribution
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/staticobjects/Marketing%20docs2%20(ShadeCash).png" width="700"/>
|
||||
https://shadecash.gitbook.io/shadecash/get-started/how-to-withdraw-relayer
|
||||
|
||||
## **Sunset**
|
||||
🚩check: the last updates; _result_: inactive since 2021
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/staticobjects/Sunset%20(Coinbook).png" width="600"/>
|
||||
|
||||
http://coinbook.app
|
||||
|
||||
.png?raw=true)
|
||||
|
||||
https://twitter.com/coinbook_com
|
||||
|
||||
## **Team**
|
||||
🚩check: public team; _result_: anon
|
||||
|
||||
|
||||
<img src="https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/staticobjects/Anon%20team%20(CIT%20Protocol).png" width="600"/>
|
||||
|
||||
https://ciaprotocol.com/#about
|
||||
|
||||
# **Summary**
|
||||

|
||||
180
Web3privacynowplatform/scoringmodel/Scoringmodel_techies.md
Normal file
|
|
@ -0,0 +1,180 @@
|
|||
# Privacy scoring modelling > Web3privacy now analytical [platform](https://github.com/Msiusko/web3privacy/tree/main/Web3privacynowplatform)
|
||||
|
||||
_Currently we are surveying developers, security engineers and researchers to find out bottle necks & potential room for growth within privacy features assessment by techies._
|
||||
|
||||
## Core user group (techies definition):
|
||||
- junior or general devs with under 1-year web3 coding experience
|
||||
- poor security auditing skills
|
||||
- general interest in privacy tech
|
||||
|
||||
## Why this group
|
||||
- general public within the devs landscape is the most vulnerable audience compared to mature decs with connections & experience
|
||||
- generalisation helps to make universal tooling & secure research from the niche approaches
|
||||
|
||||
## General scoring will consist of
|
||||
- audit check up (manual)
|
||||
- scoring features
|
||||
- dev toolkit
|
||||
- DYOR expanded track (subjective observations)
|
||||
|
||||
## Quick take from market assessment
|
||||
- devs lack the basics of security audits (while auditing companies or security engineers create piles of written that require lots of dev hours to read & more to understand)
|
||||
- case studies could help to "visualize" the assessment journey
|
||||
- DB of the malicious practices & critical bugs within the privacy landscape will come in handy for practical devs
|
||||
|
||||
**Hypothesis**: can the market create a standard of cross-project privacy features check-up increasing general privacy stack levelling?
|
||||
|
||||
**Crucial scoring context**: time on research x potential amount of privacy anti-features detection. Meaning that scoring could be scalable if more people will use it under the economy, general business & without expert knowledge level.
|
||||
|
||||
# MVP for non-techies expanded to techies
|
||||
|
||||
**Sandbox: DeFi category that has been analyzed**
|
||||
|
||||
**How to use sandbox?**
|
||||
1. Read scoring assumptions below.
|
||||
2. Give us feedback via Pull request here.
|
||||
3. You can always explore [scoring MVP](https://mirror.xyz/0x0f1F3DAf416B74DB3DE55Eb4D7513a80F4841073/90XEXa7AG_qc-VgYKs40i88xB1HF97gr1zqb-qvnif0) based on 38 DeFi project' assessment [here](https://github.com/web3privacy/web3privacy/blob/main/Web3privacynowplatform/scoringmodel/DeFi%20category%20prototype.md)
|
||||
|
||||
**important note**: here "techies" covers "juniors" & general "developers" (masses) & not aplicable to "lead", "seniors" or even "mid"-devs (core devs).
|
||||
|
||||
# Scoring model 1.2: validity track
|
||||
|
||||
_Validity track covers GitHub, Product-readiness, Team, Docs, Audit._
|
||||
|
||||
**Note**: quick assessment helps to decrease privacy dark patterns from obscure language to test-net claiming it has a "state of art privacy".
|
||||

|
||||
|
||||
## Sandbox
|
||||
|
||||
**Extended scoring 1.0**
|
||||
| Project | GitHub | Product-readiness | Team | Docs | Audit | Contributors | Licenses | Support | Score |
|
||||
| ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- | ------------- |
|
||||
| **Test project** | available & active GitHub / not (25%) | Live or 🚧 (exclusion criteria) | public team / not (25%) | available & not marketing docs / not (25%) | available & up to date third-party audit / not (25%) | external contributors outside of the team members | What licenses are in use | Some form of support available? (telegram, discord, forum) | from 0 to 100% |
|
||||
| **score** | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 12.5% | 100% |
|
||||
|
||||
**Updates 1.1**
|
||||
|
||||
**GitHub**
|
||||
* Is it in stable release, 1.0 and not an alpha or untested code?
|
||||
* Are there many PRs and Issues pending?
|
||||
* Are there external contributors outside of the team members? [Waku example](https://github.com/waku-org/go-waku)
|
||||
* What are licenses in use? [Privy Apache-2.0 license](https://github.com/privy-io/shamir-secret-sharing)
|
||||
|
||||
**example**: _Free & Open Source Software is the foundation that enables you to check whatever you want. The hoprd client is released under [GPLv3 license](https://github.com/hoprnet/hoprnet/blob/master/LICENSE) that allows you to do that (and also modify and re-distribute) Hoprn freely_
|
||||
|
||||
**Docs**
|
||||
- read the documentation: is it comprehensive?
|
||||
- how well-written are privacy & security assumptions/guarantees?
|
||||
- if aplicable: how well-written is encryption method? [example](https://developer.litprotocol.com/v3/sdk/access-control/encryption)
|
||||
- is Whitepaper marketing or dev-centric?
|
||||
|
||||
**Team**
|
||||
* Check if there are known contributors (reputation 101)
|
||||
* Check commits at GitHub
|
||||
* How many community contributors beyond core team?
|
||||
* How many technical specialists in the team?
|
||||
* How mature are core contributors (previous projects, GitHub commits)?
|
||||
|
||||
**Third-party audit**
|
||||
- Were bugs fixed? [Zokyo x Railgun_ example, p.7](https://assets.railgun.org/docs/audits/2023-02-03%20Zokyo.pdf)
|
||||
- How centralized are product updates?
|
||||
|
||||
**Infrastructure**
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| Where are the nodes (check block explorer) [Nym mainnet explorer](https://explorer.nymtech.net) | + |
|
||||
| Number of nodes (the larger the footprint the best privacy) | + |
|
||||
|
||||
**Data aggregation**
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| no email or tel number for signup | + |
|
||||
| does not implement KYC or AML | + |
|
||||
| What user information is stored? (username, IP address, last connection, wallets associate, etc) | + |
|
||||
|
||||
**Traction**
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| Amount of transactions (Dune, DeFi Lama, block explorer etc) | + |
|
||||
| number of people using it | + |
|
||||
|
||||
**Governance**
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| DAO structure (if applied) | + |
|
||||
| How centralized is the protocol governance? [Railgun_ governance docs](https://docs.railgun.org/wiki/rail-token/protocol-governance) | + |
|
||||
|
||||
**Traceability**
|
||||
|
||||
example:
|
||||
1. Use @Railway_xyz to send a private transfer to a 0zk address through a Relayer.
|
||||
2. Examine the "receipt" of that transfer on etherscan or arbiscan. You will not find: (1) sender, (2) receiver, (3) token or (4) amount anywhere in the transaction receipt.
|
||||
|
||||
https://t.co/PqkUJWwmPD
|
||||
* This is a 0zk -> 0zk transaction (sending tokens from one #DeFi user to another. You'll note that the scan has a from address but this is simply a Relayer address that pays gas to process the on-chain computation).
|
||||
* User communications with a Relayer are passed via through the @waku_org p2p gossip network, so Relayers can't know a particular message origin. In other words, even here #privacy was a big consideration throughout the tech stack not just on Etherscan.
|
||||
* The To address is simply the RAILGUN smart contract on @0xPolygon in this case. So nothing is revealed about the recipient.
|
||||
* The value that exchanged hands? #Private
|
||||
* Try to decode the input data for the transaction? It's all #encrypted.
|
||||
* So how much money exchanged hands here? Well, the short answer here is - it's #private.
|
||||
* Only the sender and recipient will know. There will be #zeroknowledge about it unless they choose to reveal the transaction information.
|
||||
|
||||
# Backlog
|
||||
|
||||
## General
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| Immutability | + |
|
||||
| Decentralised throughout, including hosting | + |
|
||||
| Permissionless & accessible to all | + |
|
||||
| Open-source | + |
|
||||
|
||||
## Privacy policy
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| Privacy Policy content [Railway zero data aggregation PP](https://www.railway.xyz/privacy.html) | + |
|
||||
| Non-vague and non-intrusive privacy policy | + |
|
||||
|
||||
## Storage
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| e2e encrypted LOCAL storage | + |
|
||||
| Where is it stored? (centralized server, certain jurisdictions, on-chain, in browser/local cache) | + |
|
||||
|
||||
## Privacy execution
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| p2p / no central server | + |
|
||||
| Trustless - No ID required (this is where ZKs are useful) | + |
|
||||
|
||||
**example**: "with the unirep protocol we're building an explorer that shows all the things happening in the system. So a user could see their epoch keys and attestations and see how they're distinct in the system. One thing we might do is write what can and can't be determined about the different identifiers".
|
||||
|
||||
## Testing
|
||||
| Scoring | Techie |
|
||||
| ------------- | ------------- |
|
||||
| try to trace a transaction | + |
|
||||
| Other tooling to verify e.g. block explorers | + |
|
||||
|
||||
## Hardcore
|
||||
|
||||
from community
|
||||
|
||||
* use a packet inspection tool such as #Wireshark to check all packets coming into your machine and going out
|
||||
* using something like https://charlesproxy.com to see all the traffic
|
||||
* Android: Feel free to test it at [Exodus Privacy](https://exodus-privacy.eu.org/en/), a friendly service to investigate Android apps.
|
||||
* Android: check https://f-droid.org and verify the “no anti-features” tag (like dependency on third-party services). [Example](https://f-droid.org/en/packages/com.nighthawkapps.wallet.android/)
|
||||
|
||||
# ETHSecurity community recommendations
|
||||
_We asked Ethereum security chat members to share guides that devs could use to check privacy features of a given dApp or a protocol. Here are the first tips:_
|
||||
|
||||
[DeFiSafety](https://medium.com/defi-safety/introducing-our-0-9-process-79ba88f8bba4): "a clear list of what a dev should add to a protocol (over and above the software)"
|
||||
|
||||
**Officercia** recommendations
|
||||
- [The ultimate security checklist](https://www.beirao.xyz/blog/Security-checklist)
|
||||
- [Tips for Solidity Code Auditors](https://github.com/OffcierCia/tips-solidity-code-auditors)
|
||||
- [Minimum viable security plans from Trail of Bits](https://docs.google.com/document/d/1-_0Wlwch_vtkPM4F-SdEXLjQYaYT7KoPlU2rjt7tkLQ/edit)
|
||||
- [Opinionated security and code quality standard for Solidity smart contracts](www.github.com/Rari-Capital/solcurity)
|
||||
|
||||
[SCSVS](https://github.com/ComposableSecurity/SCSVS/): Smart Contract Security Verification Standard
|
||||
|
||||
[EthTrust](https://entethalliance.github.io/eta-registry/security-levels-spec.html): EEA EthTrust Security Levels Specification v-after-1
|
||||
627
Web3privacynowplatform/scoringmodel/Survey/Readme.md
Normal file
|
|
@ -0,0 +1,627 @@
|
|||
# [Survey](https://docs.google.com/spreadsheets/d/1JWpAsGL10UTsVeuIVbouzUxRjaSPUAamxcbFljXuUWE/edit?usp=sharing)
|
||||
We asked 50+ privacy opinion leaders how they will attest privacy claims behind their projects.
|
||||
|
||||
**Approach**:
|
||||
- we made a survey on how privacy projects recommend analysing if they are private or not.
|
||||
- answers were assembled into 1 Excel sheet to be further analysed
|
||||
|
||||
## **Fileverse**
|
||||
|
||||
| Answers | Observations | Product feature |
|
||||
| ------------- |------------- |------------- |
|
||||
| open sourcing our work | open source non-techies should know what "open source" means & how to measure it (solution: Open source 101 education) | open source 101 (short version) |
|
||||
| you literally generate and download your own e2ee keys | key ownership is another knowledge person should know (contrast: Google or Meta "owns" your ID/key) + e2ee 101 is a must here | e2ee 101 |
|
||||
| documentation | clicking on the documentation link & understanding it are different skills | documentation: exists/missing (+/-) |
|
||||
| social recovery options | social recovery is a less techy assessment & is linked to a persona (data ownership) | social recovery 101 |
|
||||
|
||||
## **Lava Network**
|
||||
|
||||
| Answers | Observations | Product feature |
|
||||
| ------------- |------------- |------------- |
|
||||
| starting with our litepaper | "read the docs" is a popular answer without any third-party attestation that docs are correct, care for privacy etc | in the future: collab with a security audit companies to create a new docs audit service description when a third-party will attest privacy-features of the initial idea x tooling description |
|
||||
| further questions feel free to drop them in our discord | Discord serves as a two-way comms platform (but depends on the project) & it creates additional dependence of user on the core team | - |
|
||||
|
||||
## **Holonym**
|
||||
| Answers | Observations | Product feature |
|
||||
| ------------- |------------- |------------- |
|
||||
| Check their website or docs | "check" is a highly abstract action related to the website or docs -> extract value should be related to understanding "privacy"-validity markers | website checklist (1-2-3-4-5..., yes/no validity) |
|
||||
| If they vaguely say “data is kept private” and provide no explanation how, run | "private data explainers" needed to be defined within use-cases (case studies for the market) | case studies "private data" explainers |
|
||||
| If they provide an explanation, check with an expert or DYOR | - | DYOR (that's our platform) |
|
||||
|
||||
## **Spinner cash**
|
||||
| Answers | Observations | Product feature |
|
||||
| ------------- |------------- |------------- |
|
||||
| code is law | the more ideological language is on the website - the harder to navigate the factual privacy features | missing 3rd party audit potential risks 101 |
|
||||
| So how about "don't trust, verify"? But to verify, it would require certain technical skills... like reading source code 😅 | source code reading is a highly technical skill (moreover: Ethereum dev could struggle with Solana code & vice versa) | 3rd party list (yes/no) from security audit agencies to independent security engineers (+their reputation 101 in later versions) |
|
||||
|We hope to bring in 3rd party auditors at some point | 3rd party list is needed here to be transformed into privacy signalling features | - |
|
||||
|
||||
## **Session**
|
||||
|
||||
Answers
|
||||
- There is the Session code audit
|
||||
- See what's being said in (non-paid) media: reviews, articles, etc.
|
||||
|
||||
_Observations_:
|
||||
- existing audit is a plus (even if code could be updated, audit could be partial etc)
|
||||
- hard to define non-paid media placements, but existing media credibility (reco by trusted people like Vitalik - is a plus)
|
||||
|
||||
_Product feature_:
|
||||
- code audit (yes/no). Case studies (how those audits could look alike with active links)
|
||||
- simplified media analysis 101
|
||||
|
||||
## **ZKBob**
|
||||
|
||||
Answers
|
||||
- whether the solution forces users to preserve their privacy or if it's the user's responsibility. For example, Tornado Cash increases anonymity by requiring users to deposit a specific amount but doesn't require using different addresses for withdrawals
|
||||
- zkBOB doesn't force specific amounts or address usage, but encourages the use of new withdrawal addresses by rewarding them with a small amount of native coins that can be used in the next transaction to pay for gas.
|
||||
- How the components of the protocol communicate with each other and if users can replace any components is another important aspect.
|
||||
- In the case of zkBOB, the pool contracts are the core component, and the user needs to trust the zkBOB development team regarding privacy leaks in the rest of infrastructure: UI and the sequencer. However, the project roadmap includes plans to address these concerns.
|
||||
- Since privacy-preserving solutions on the blockchain involve complex mathematical concepts that may be difficult for non-techie individuals to understand, there will always be trust assumptions for this part of the solution.
|
||||
- "The only way for non-techie people to reduce risks is to seek expert advice or do extensive research before using such solutions.
|
||||
- For zkBOB, it's worth noting that the project is open source, the part of the protocol related to zero-knowledge was audited, and the team does its best to support documentation that's up-to-date and clear for ordinary users."
|
||||
|
||||
_Observations_:
|
||||
- interesting approach opposite to "optional privacy" - push the person to gain privacy by performing extra actions, so privacy will be "tangible"
|
||||
- privacy culture could be gamified & serve as a privacy 101 (new withdrawal addresses generation)
|
||||
- "protocol components" are highly-techy issues to track
|
||||
- ZK decentralisation (to be achieved) should be communicated (if you don't trust project team - that's a risk)
|
||||
- trust assumption should be expanded within 101 (where exactly person "delegate" trust to the project)
|
||||
- audit & trust assumptions could co-exist in 1 project, but it's critical to understand risk categories for each component of "trust"/"privacy" relations
|
||||
|
||||
_Product feature_:
|
||||
- trust assumptions 101
|
||||
- privacy in ZK 101
|
||||
- later on - case studies when solutions actively embed privacy education within the workflow
|
||||
|
||||
## **Litentry**
|
||||
|
||||
Answers:
|
||||
- you can start by reading Litentry’s explainers first
|
||||
- then maybe then read through other privacy solutions to make the comparison?
|
||||
|
||||
Observations:
|
||||
- explainers could explain privacy features but should be helpful to make self-research (to be investigated)
|
||||
- not many privacy projects compare themselves within privacy features (extreme exception: Samurai team attack Wasabi) - opportunity for us
|
||||
|
||||
_Product feature_
|
||||
- future: privacy features comparison within solutions (creating a comprehensive privacy market metrics set)
|
||||
|
||||
## **BrightID**
|
||||
|
||||
Answers:
|
||||
- You could rationalize from the fact that it does not ask you for any personally identifying information directly, so there is nothing to preserve and keep it safe in its infrastructure.
|
||||
- technical things you could ask a technical person you trust to look at its oss code.
|
||||
|
||||
_Observations:_
|
||||
- if there's nothing to ask - there's nothing to hide, - interesting assumption, but services could collect data without asking (like IP)
|
||||
- need extra technical help to analyse the code (potential for a privacy QA automation)
|
||||
|
||||
_Product features:_
|
||||
- privacy data leakages 101
|
||||
|
||||
## **Swarm**
|
||||
|
||||
Answers
|
||||
- reading our whitepaper, which provides a comprehensive overview of Swarm's technology and how it achieves privacy
|
||||
|
||||
_Observations_:
|
||||
- whitepaper is too "heavy" instrument for people with a short attention span & in need of quick attestations. Moreover, it's not up to date, usually
|
||||
|
||||
_Product feature_
|
||||
- web3 docs 101 (basic description in relation to privacy)
|
||||
|
||||
## **Railgun**
|
||||
|
||||
Answers
|
||||
- Use @Railway_xyz to send a private transfer to a 0zk address through a Relayer.
|
||||
- Examine the "receipt" of that transfer on etherscan or arbiscan. You will not find: (1) sender, (2) receiver, (3) token or (4) amount anywhere in the transaction receipt.
|
||||
- There's a ton a technical person can do to verify but there's also a litmus test of #privacy that anyone can do: https://t.co/PqkUJWwmPD
|
||||
- "This is a 0zk -> 0zk transaction (sending tokens from one #DeFi user to another). You'll note in the scan has a from address but this is simply a Relayer address that pays gas to process the on-chain computation.
|
||||
- User communications with a Relayer are passed via through the @waku_org p2p gossip network, so Relayers can't know a particular message origin. In other words, even here #privacy was a big consideration throughout the tech stack not just on Etherscan.
|
||||
- The To address is simply the RAILGUN smart contract on @0xPolygon in this case. So nothing is revealed about the recipient.
|
||||
- The value that exchanged hands? #Private
|
||||
- Try to decode the input data for the transaction? It's all #encrypted.
|
||||
- So how much money is exchanged hands here? Well, the short answer here is - it's #private. Only the sender and recipient will know. There will be #zeroknowledge about it unless they choose to reveal the transaction information.
|
||||
|
||||
_Observations_
|
||||
- general web3 101 is needed for a person to self-check privacy (what is 0zk address, relayer, etherscan etc)
|
||||
- simple instructions on transaction traceability will help to self-check sender-receiver-token-ammount links. Input & observations criteria (possible framework?) will help here (short instruction).
|
||||
|
||||
_Product feature_
|
||||
- transaction traceability 101 (the basics on Etherscan example)
|
||||
|
||||
## **Penumbra**
|
||||
|
||||
Answers:
|
||||
- maybe look for people you trust that are able to analyze the technical solution for its privacy merits and then get their opinion? it's prob difficult to analyze a technical protocol with a non-technical analysis.
|
||||
- what you're asking about relates to a more holistic assessment of a protocol and its attributes, so that should be within the scope of a research function moreso than a security audit function.
|
||||
|
||||
_Observations_:
|
||||
- complex technical protocols are inaccessible to the general public unless a third party completes a comprehensive audit from architecture to data leakages analysis
|
||||
|
||||
_Product feature:_
|
||||
- a checklist of when you need a "tech" person help to attest privacy features & when not (with a focus on a second scenario)
|
||||
|
||||
## **HOPR**
|
||||
|
||||
Answers:
|
||||
- FOSS. Free & Open Source Software is the foundation that enables you to check whatever you want. The hoprd client is released under GPLv3 license that allows you to do that (and also modify and re-distribute) hoprd freely.
|
||||
- Code quality. Open source code should be readable to be helpful to you! To that end, we enforce code quality via linters for Typescript
|
||||
https://github.com/hoprnet/hoprnet/blob/df7bc88517329472adbfe73bd4a22bddd5cfbcc9/package.json#L46… and for our Rust code: https://github.com/hoprnet/hoprnet/blob/master/rustfmt.toml…
|
||||
- Tools. So far we released tools such as http://DERP.hoprnet.org or http://mint.hoprnet.org (which in turn are obviously also FOSS!) that show shortcomings of existing technologies. We will keep building such tools also for HOPR itself. The exact checks you'd do depend on the application that actually uses HOPR E.g. on #RPCh we're thinking of installing a VPN server on the RPCh exit node which would visualize requests via DERP: https://twitter.com/hoprnet/status/1596896868377792520
|
||||
- If you want to go hardcore, you could use a packet inspection tool such as #Wireshark to check all packets coming into your machine and going out. You will notice that you cannot tell anything from these packets - thanks to the Sphinx packet format that we use at HOPR: https://twitter.com/hoprnet/status/1572601550379311104
|
||||
|
||||
_Observations_:
|
||||
- open-source basics are needed to have trust assumption that FOSS are more trustable compared to Apple, Mozilla etc (or not more, but it's a sign of reputation directly related to trust).
|
||||
- readable code could be a standard for privacy attestations (for techies, obviously). If it's obscured & not audit-friendly - flag
|
||||
- tools like DERP are good for transactions & tools ops traceability & should be created by the community (potential direction for us) - "DERP" for "everything"
|
||||
- packets traceability is a nightmare for non-techie but could be a "level up" needed by a tech person to understand privacy leakages (via "extended audit tooling" track)
|
||||
|
||||
_Product feature_
|
||||
- "DERP"-alike tool for the future privacy script-based "check-up" product releases
|
||||
|
||||
## **Waku**
|
||||
|
||||
Answers:
|
||||
- rfc.vac.dev is a good start. The RFC repository contains the specification of Waku and other protocols. In terms of @ethstatus's privacy claims. It is good to first look at the base layer: @waku_org
|
||||
- The RFCs describe the protocol and also contain security assumptions/guarantees section."
|
||||
- The target audience are researchers and maintainers of Waku implementations. Not the easiest thing to read!
|
||||
|
||||
_Observations_:
|
||||
- bits of https://vac.dev/wakuv2-relay-anon could be used for educational materials, but it's still highly-technical (or even security officer-centric, researcher-ready)
|
||||
|
||||
_Product feature_
|
||||
- "attacks" (threats) 101
|
||||
|
||||
## **Rotki**
|
||||
|
||||
Answers:
|
||||
- Don't think u can. Gotta trust either me or someone who can read code
|
||||
- The simplest thing a non-techie person can understand are:
|
||||
- Local application with all data stored in a local encrypted database (private by design)
|
||||
- Opensource, so your techy friend can see we are not lying. It really isn't complicated imo.
|
||||
- To be 100% sure read code
|
||||
- But it does not take an expert to understand that an application that you download, run locally and keeps all data locally is 1000x more private than a webapp. We have been brainwashed to call webapps, as "apps" now.
|
||||
|
||||
_Observations_:
|
||||
- Trust assumptions, again, are related to high risk. Trust assumptions use-cases could share light on different scenarios of trust compromises.
|
||||
- encryption 101 is needed relating to decentralised or local storage
|
||||
- open-source could be a "nice to have" feature in relation to decreasing the amount of centralisation or control
|
||||
- local "storage" vs "webapps" privacy scenarios are needed to explain control over the privacy leakages / negative scenarios
|
||||
|
||||
_Product feature_
|
||||
- encryption 101
|
||||
|
||||
## **Webb**
|
||||
|
||||
Answers:
|
||||
- you need to analyze the data they create through transactions. If that data (and metadata) can be analyzed for patterns then that can help define the degree of privacy of the solution.
|
||||
- For our bridge solution, this is akin to rebuilding the tx graph and seeing if flows through such a graph can be identified. The main actions in our system are deposit, transfers, and withdrawals. We use the same zero-knowledge proof-based ideas to make it harder to track
|
||||
|
||||
_Observations_:
|
||||
- Zero-knowledge magic will lead to lots of privacy breakages.
|
||||
|
||||
_Product feature_
|
||||
- ZK x privacy 101 for future releases (like decentralised sequencer 101)
|
||||
|
||||
## **Boring protocol**
|
||||
|
||||
Answers:
|
||||
- The "no logs" claims are generally very ambiguous. We make a point to know as little as technically possible about our users. We only know the bare minimum required to make the network function.
|
||||
- All we know is your wallet pubkey, with which we issue and assign to a network key.
|
||||
|
||||
_Observations_:
|
||||
- when the project claims "we don't know" - exactly this should be attested (returning to "DERP" alike solution)
|
||||
|
||||
_Product feature_
|
||||
- pubkey, network key, viewing key etc 101
|
||||
|
||||
## **Lit protocol**
|
||||
|
||||
Answers:
|
||||
- State of Network is available right here: https://t.co/sgaOX5SPga
|
||||
|
||||
_Observations_:
|
||||
- state of the network isn't linked to privacy - false assumption (even if, it's too hard for a non-techie to double-check it)
|
||||
|
||||
## **Alter network**
|
||||
|
||||
Answers:
|
||||
- Try the #dapp and join the chatroom for @AlterDapp community
|
||||
- You can check out this video to see how to create an account on mobile: https://youtu.be/ZgpCHDnR9WU
|
||||
- The discord has a lot of resources as well, depending on what you need.
|
||||
|
||||
**Observations**:
|
||||
- Product usage rarely has sophisticated UX/UI that could correspond privacy features in a simple way with proves
|
||||
- Projects use socials like Discord to share product-centric materials (from analytics to audits) while websites are not often updated
|
||||
|
||||
## **Sons of crypto**
|
||||
|
||||
Answers:
|
||||
- We have no (google) analytics or tracking
|
||||
- We do not run any backend
|
||||
- We will have built-in mixers
|
||||
- We don't know or what to know who or where users are. For non-techie that would not be straightforward.
|
||||
- Perhaps using something like https://charlesproxy.com to see all the traffic. Still fairly techie though.
|
||||
- For devs all of our code is open source on github, anyone can read it.
|
||||
|
||||
_Observations_:
|
||||
- Tracking could be by a third party like Google (also compromises privacy & fake conscious consent)
|
||||
- External services like Charleproxy is really valuable, but create a burden on a non-techie, because of it's complexity (but will work for a techie)
|
||||
- GitHub (updated, alive) could be a checkmark (formal)
|
||||
|
||||
**Product feature**
|
||||
- GitHub basic score (flag system could be a part of the second product release)
|
||||
- List of external third-party resources in a Wiki (for those, who like to make extra effort -> influence micro-services creation)
|
||||
|
||||
## **Orbis**
|
||||
|
||||
Answers:
|
||||
- You can check our open-sourced SDK, but that would require people to read some code :) https://t.co/iiA7lSaDdn
|
||||
|
||||
_Observations_:
|
||||
- SDK is just too technical
|
||||
|
||||
## **Nighthawk Wallet**
|
||||
|
||||
Answers:
|
||||
- It’s been a while since @NighthawkWallet APK was analyzed for privacy concerns. Feel free to test it at @ExodusPrivacy, a friendly service to investigate Android apps.
|
||||
- You can also obtain the @NighthawkWallet APK built with @fdroidorg and verify the “no anti-features” tag.
|
||||
- We’ve worked hard to remove dependency on third-party services and strictly require users’ consent before opting into sharing information: https://t.co/YwYd4RUeVh
|
||||
- Anti-Features are organized into “flags” that packagers can use to mark apps, warning of possibly undesirable behaviour from the user’s perspective, often serving the interest of the developer or a third party: https://t.co/LEaBIh8LV7"
|
||||
|
||||
_Observations_:
|
||||
- existing third-party allows checking privacy validity (but it's not up to date)
|
||||
- "no anti-features" should be researched further for qualitative recommendations (DYOR track)
|
||||
- consent in the web3 privacy services is a field for further research (how it differs from web3 GDPR-centric consent, do services share their state of privacy features etc?)
|
||||
|
||||
_Product feature_
|
||||
- "Anti-features" 101
|
||||
|
||||
## **KILT Protocol**
|
||||
|
||||
Answers:
|
||||
KILT preserves privacy in the same way paper or plastic credentials do:
|
||||
|
||||
1. they are not stored on any central entity but totally decentralised in the wallets of their owners.
|
||||
2. users decide for what reason they share a credential with whom.
|
||||
3. one can share credentials partially" A DID is created on the user‘s device. Like your blockchain keypair. It’s an identifier like your face, your fingerprint or your signature. It’s not issued by any entity. This way it’s always decentralised and does not have a decentralisation status.
|
||||
|
||||
_Observations_:
|
||||
- web2 product comparison with the web3 is a valuable hint to not necessarily expect 100% privacy if it's a format, or product feature (not a bug) - applicable to a whole category
|
||||
- "free to share" ability could be communicated as a person's agency over privacy (similar to the "viewing key" approach in ZK)
|
||||
- a link between the different parts of DID should be more explored (like how age or geo could lead to identity discovery)
|
||||
|
||||
_Product feature_
|
||||
- did 101 (with a focus on the linkage between different data types)
|
||||
|
||||
## **Onionclub**
|
||||
|
||||
Answers:
|
||||
- actually, privacy is by default on our platform. It's not an option!
|
||||
- So, every user will have this enabled and if they want to be doxxed then they need to jump through some hoops.
|
||||
|
||||
_Observations_:
|
||||
- lack clear attestation
|
||||
|
||||
_Product feature_
|
||||
- web3 comms 101 (with a focus on misleading comms that create an obscure understanding of the tech/product)
|
||||
|
||||
## **Sismo**
|
||||
|
||||
Answers:
|
||||
- Here are the public resources we have around the core of our ZK systems:
|
||||
- Commitment mapper https://docs.sismo.io/sismo-docs/technical-concepts/commitment-mapper…
|
||||
- Hydra-S1 ZK Scheme https://docs.sismo.io/sismo-docs/technical-concepts/hydra-zk-proving-schemes…
|
||||
- Privacy & Security FAQ (the less technical part): https://t.co/M3eVLoYeUK
|
||||
|
||||
_Observations_:
|
||||
- all concepts are too technical, & FAQ is missing from the docs
|
||||
|
||||
## **Krebit**
|
||||
|
||||
Answers:
|
||||
- Privacy-preserving: your credential's claims are stored encrypted off-chain.
|
||||
- Self-sovereign: you control the access conditions to read your private data
|
||||
- This is possible thanks to @LitProtocol and @ceramicnetwork
|
||||
|
||||
_Observations_
|
||||
- self-sovereignty is still an obscure concept for many people online. Especially, when technical concepts like "access conditions" are shared with people
|
||||
- it's important to share public audits if a product uses privacy features of a third party (the more services are involved in the tech link - the easier is to obscure people's attention & understanding of privacy stack)
|
||||
|
||||
## **Puma browser**
|
||||
|
||||
Answers:
|
||||
One of the reasons we started focusing more on enabling novel use-cases like ENS/HNS/IPFS and others is because it's really easy to demo in 10-15 seconds and prove, vs privacy is much harder to both demo and prove beyond company reputation.
|
||||
|
||||
_Observations_:
|
||||
- marketing language creates a vague understanding of privacy features. Moreover, people are bombarded by web3 slang, and third-party services & can't test privacy features with ease
|
||||
|
||||
## **Hideyour.cash**
|
||||
|
||||
Answers:
|
||||
- We’re in the process to conduct a security audit with a full report when going to mainnet.
|
||||
- Our code is open source in case you wanna ask someone from your trust.
|
||||
|
||||
_Observations_:
|
||||
- would be good if services will share their security audit plans with a clear roadmap. Having a public commitment to privacy could be a part of positive behavior on behalf of the tech teams
|
||||
|
||||
_Product feature_
|
||||
- security audits 101 (basics)
|
||||
|
||||
## **Spook**
|
||||
|
||||
Answers:
|
||||
- If you’re non-technical you won’t be able to verify it yourself.
|
||||
- You need this information from a trusted source that has done the job of checking its privacy.
|
||||
|
||||
_Observations_:
|
||||
- which leads to a necessity to have three actors relations: product-"trusted source"-person ("privacy trilemma")
|
||||
|
||||
_Product feature_
|
||||
- trusted sources checklist (&/or a list)
|
||||
|
||||
## **Elusiv**
|
||||
|
||||
Answers:
|
||||
- Once we are live, detailed docs including our whitepaper will be released!
|
||||
- you can expect more explanatory content covering various topics around privacy, ZKPs, MPC and more.
|
||||
|
||||
_Observations_:
|
||||
- no whitepaper, no docs - could be a soft flag on privacy features (more open data = higher potential privacy rate). Where "having a whitepaper" is a plus, but not a silver bullet
|
||||
|
||||
_Product feature_
|
||||
- web3 open-source checklist (soft screening like whitepaper (yes/no), docs (yes/no) etc)
|
||||
|
||||
## **Beam**
|
||||
|
||||
Answers:
|
||||
- You can read Beams whitepaper
|
||||
- I also recommend reading the Documentation
|
||||
- you can reach me here on Twitter, on Telegram @maxnflaxl or on Discord Maxnflaxl#8141
|
||||
|
||||
_Observations_:
|
||||
- many projects still project "trust source" on themselves. Without sharing the results of hacker bounties, public QA, whitehacker audits & so on. The culture of third-party public discussions is almost non-existent (to be researched why except the price of audits)
|
||||
|
||||
## **Findora**
|
||||
|
||||
Answers:
|
||||
Dapps using our privacy SDK will allow their users to transact with privacy. The evidence can be found on our block explorer when one attempts to view the details.
|
||||
|
||||
_Observations_:
|
||||
- block explorers aren't made for the general public to understand the data flow (this could lead in the future to a human-friendly block explorer x privacy education)
|
||||
|
||||
## **Leo wallet**
|
||||
|
||||
Answers:
|
||||
- Here's a talk by our co-founder/CTO discussing Zero-Knowledge Proofs in general and some features our wallet utilizes to increase privacy (e.g. single-use addresses): https://t.co/BLeKu2ghmS
|
||||
|
||||
_Observations_:
|
||||
- visuals complimentary to the interview help to navigate non-techies with ease on the privacy subject. One of the rare projects talking about the limitations of their tech (o ZK tech in general). But still, everything related to ZK (proving schemes, for example) is highly technical.
|
||||
- ZK-products will see lots of exploitations & bugs in the future, so it's important to educate people on the state of general tech, so they won't transfer all the sensitive data because of the hype, attention etc
|
||||
|
||||
_Product feature_
|
||||
- ZK 101 (with a focus on privacy, not scalability)
|
||||
|
||||
## **Scala**
|
||||
|
||||
Answers:
|
||||
- You should probably start here: https://wiki.scalaproject.io and if you have questions send us a DM.
|
||||
|
||||
_Observations_:
|
||||
- again, projects don't care about privacy validation as if it's a default trustless state. Which is incorrect.
|
||||
- the general wiki isn't the best source of knowledge (one opposite positive example: Waku)
|
||||
|
||||
## **Media network**
|
||||
|
||||
Answers:
|
||||
- Thanks to the blockchain and smart contracts, your personal and payment information is always secure.
|
||||
- Communication between clients and providers is always encrypted.
|
||||
- The client only needs to disclose the origin (i.e., the back-end IP) for the CDN marketplace and the Legacy dCDN.
|
||||
|
||||
_Observations_:
|
||||
- people could be misinformed about the way blockchain works thinking that security means privacy
|
||||
- encryption doesn't mean you don't leak your data to RPC, hosting etc. Cross-services/products relations to data leakages should become a market standard of comms (example: using one privacy tool that is private, but connecting it to another that leaks your data equals privacy breaches).
|
||||
|
||||
_Product feature_
|
||||
- web3 privacy 101 (focus on a misleading comms like blockchain security equals privacy)
|
||||
|
||||
## **Privacy & Scalability**
|
||||
|
||||
Answers:
|
||||
- one approach might be looking at the public data from the system. If you see user identifiers being used only once that's perhaps helpful? But a non-technical person doesn't know if identifiers are truly random, or if they're backdoored somehow.
|
||||
- With the unirep protocol we're building an explorer that shows all the things happening in the system. So a user could see their epoch keys and attestations and see how they're distinct in the system. One thing we might do is write what can and can't be determined about the different identifiers.
|
||||
|
||||
_Observations_:
|
||||
- hackathons on user identification could help to empower product privacy. Whitehackers role in a privacy market could be uplifted to a degree of product self-check/health check providing additional avenues for a third-parties to contribute to the open-source meaningfully.
|
||||
- identifiers could be created with a maximum anonymity set (and almost no linkage to a real person unlike a Covid passport)
|
||||
|
||||
_Product feature_
|
||||
- different self-check recommendations by security audits, white hackers as a supplement (how would you test product privacy)
|
||||
|
||||
## **Automata**
|
||||
|
||||
Answers:
|
||||
- You should go to the very beginning of the medium articles. There is explained how the architecture works:
|
||||
- https://medium.com/atanetwork/whats-automata-i-the-last-puzzle-piece-to-web-3-0-ea8a0af5840e
|
||||
https://medium.com/atanetwork/whats-automata-ii-protocol-overview-witness-7c1fc2232655
|
||||
- https://medium.com/atanetwork/whats-automata-iv-conveyor-93c9335e4f43"
|
||||
|
||||
_Observations_:
|
||||
- all materials are outdated & not supplied by a third-party attestation
|
||||
- medium is a centralised platform that could be edited at any time (read: information could be forged)
|
||||
- projects are creating long-reads as if people have a conscious need to dive deep on their journey of a product audit (misconception or you could say "web3 privacy products biases")
|
||||
|
||||
_Product feature_
|
||||
- part of the wiki: web3 privacy products biases (in relation to privacy features x user experience)
|
||||
|
||||
## **Aleo**
|
||||
|
||||
Answers:
|
||||
- I'd start with the official Blog articles: www.aleo.org/post/welcome-to-aleo
|
||||
https://www.aleo.org/post/zero-knowledge-primitives-by-aleo
|
||||
- also there are so many videos on this topic you can find in 📸┃user-content our community has so many contributions and rich diversity of content
|
||||
_Observations_:
|
||||
- products or ecosystem bombard people with messy content the same way as corporations (so answers can't be found fast & with the 1 link)
|
||||
|
||||
## **MASQ**
|
||||
|
||||
Answers:
|
||||
- Join our beta testing group and simply try it for yourself!
|
||||
- You can run any local and in-browser IP tests you want, and use other tools to see how the data is transported to and from your machine.
|
||||
- As a non-techie the first start is simply to check an IP checker website while using
|
||||
|
||||
_Observations_:
|
||||
- testing group or phase is a healthy point to the ecosystem & understanding the state of privacy and communal trust (test sandbox with a friendly UX/UI could be a solution here)
|
||||
- data transportation is a challenge (here we get back with the "DERP") to be explored
|
||||
|
||||
_Product feature_
|
||||
- web3-native IP-checker for a beta version
|
||||
- web3-native privacy features checker to be R&D (what could be automated & coded for QA-automation)
|
||||
|
||||
## **Lokinet**
|
||||
|
||||
Answers:
|
||||
- user education would absolutely be how.
|
||||
- To be fair lokinet's docs aren't really there rn, it's always on the todo list and never really gets done.
|
||||
- once you do all the user education you can, you get to the point where you see that privacy is more of a bonus to seal the deal than a primary feature from the perspective of the consumer-grade user.
|
||||
- ideally, we don't want Lokinet to leak anything at all.
|
||||
- net usage statistics tools from projects like pihole provide great visualizations for some of it.
|
||||
- I am sure there are ones for netflow data too not just dns.
|
||||
|
||||
_Observations_:
|
||||
- docs validity & proficiency is a hard field to analyse. Even the most up-to-date docs could be obscure & vague.
|
||||
- privacy as a bonus field should be more explored (when a person moves from a user-friendly, let's say, dVPN to a really private one) & mapped down as a user-flow
|
||||
- pihole is highly complex for a non-techie, but we could encourage services to prove via self-tests (blog posts, videos) when they test & prove how exactly private their services are raising a culture of privacy
|
||||
|
||||
_Product feature_
|
||||
- "net usage stats" services guide for the end user (but with a focus on empowering product managers to incorporate third-party tools to self-check their products & publicly report on their privacy features)
|
||||
|
||||
## **ActiList**
|
||||
|
||||
Answers:
|
||||
We are running on the Secret Network blockchain, you can check out http://SCRT.network for more information.
|
||||
|
||||
_Observations_:
|
||||
- product is obscuring the state of privacy to a bigger ecosystem entity without simple proves (usually, because such projects lacks privacy/security engineers in their teams)
|
||||
|
||||
## **Cheqd**
|
||||
|
||||
Answers:
|
||||
- You can start by learning about verifiable credentials, decentralised identifiers(DID), and the concept of Self-Sovereign identity.
|
||||
- cheqd is quite technical, and in order to understand why it is privacy-preserving, you'll need to get familiar with some terms.
|
||||
- "You can also learn more about each of the components of the network, the credential types, co-clots of payment rails and verification by visiting our learn pages
|
||||
https://t.co/8OQ0Fav16W" ("Concepts of payment rails")
|
||||
- you'll find a range of useful content and project progress on our blog. If you have any questions, you can jump on our official telegram channel or tweet us: https://t.co/wHRkrrJ3F0"
|
||||
|
||||
_Observations_:
|
||||
- verifiable credentials are still highly technical (although, Dock is trying to simplify end-user understanding) in times when DID is one of the most common use-cases for the web3. Technical complexity created a challenge for non-techie to understand the state of privacy (especially, when it requires dozens of ours of reading materials & new skills development like doc reading, code analysis etc)
|
||||
|
||||
_Product feature_
|
||||
- privacy-preserving vocabulary
|
||||
|
||||
## **PirateChain**
|
||||
|
||||
Answers:
|
||||
Look at the block explorer and see if you can figure out how much ARRR is in a wallet
|
||||
|
||||
_Observations_:
|
||||
- obscure & too technical
|
||||
|
||||
## **Obscuro**
|
||||
|
||||
Answers:
|
||||
- we'll build tools that have been audited by trusted authorities to verify attestation of software versions along with audits showing the software doesn't leak privacy
|
||||
- although superficial, our block explorers will demonstrate privacy"
|
||||
- anyone can run a node and use simple network tools to verify data flowing is encrypted
|
||||
- Provide education on how TEEs preserve privacy and the things to look out for"
|
||||
- We'll deploy a game with significant funds that can only be won by breaking Obscuro's privacy. As long as the game isn't won, users can be confident privacy remains intact.
|
||||
|
||||
_Observations_:
|
||||
- "trusted authorities" should be investigated: what are their types, why they are "authorities", who authorise them etc
|
||||
- block explorers demonstrate privacy to a tech people
|
||||
- "anyone can run a node" is a false concept, because it's a highly technical procedure
|
||||
- privacy gamification test is a nice demonstration of "unbreakability" (or a public commitment to privacy) - it's similar to whitehackers bounties
|
||||
|
||||
_Product feature_
|
||||
- examples of how products enhance privacy creatively (like a game mention by Obscuro) -> potential market benchmarks
|
||||
|
||||
## **SendingMe**
|
||||
|
||||
Answers:
|
||||
- you can visit @Sending_Network account to learn more about what is under the hood
|
||||
- our GitBook is pretty easy to read even if you are not techie :)
|
||||
|
||||
_Observations_:
|
||||
- too technical
|
||||
|
||||
## **Mysterium Network**
|
||||
|
||||
Answers:
|
||||
- we would recommend our docs: https://docs.mysterium.network
|
||||
- Also here is a study on decentralized VPN (featuring us) by @NorthwesternU, thread + paper here: https://twitter.com/MysteriumNet/status/1619616182964994049"
|
||||
|
||||
_Observations_:
|
||||
- third party study could be a nice entry into a category understanding (not directly linked with the project, team)
|
||||
|
||||
_Product feature_
|
||||
- useful links (like dVPN studies in a DYOR section)
|
||||
|
||||
## **nix-bitcoin**
|
||||
|
||||
Answers:
|
||||
- For one, you need to be fairly technical to setup nix-bitcoin at this point.
|
||||
- One important aspect is whether all outbound connections are tunnelled through Tor by default.
|
||||
- You could check the generated configuration files. For example, make sure that proxy=127.0.0.1:9050 is in fact set in /var/lib/bitcoind/bitcoin.conf.
|
||||
_Observations_:
|
||||
- if a product requires tech proficiency - it's important to highlight it (entry-level into tech understanding)
|
||||
- Tor is a plus1 to privacy, but not a silver bullet (important to understand "privacy enhancement" & not just "1 solution to general privacy")
|
||||
- configuration files can't be checked by non-techies (but could be used as a signal on privacy transparency - if service hides clues on how to self-check it's privacy credibility or not)
|
||||
|
||||
_Product feature_
|
||||
- "privacy stack" enhancement prototyping (1 solution + 1 solution = privacy "2x" (like Session messenger + dVPN)
|
||||
|
||||
## **Litecash**
|
||||
|
||||
Answers:
|
||||
- Litecash is the first fork of BEAM and we tweaked the fees to zero, and less congested to keep lightning-fast transaction along with a sustainable coin supply for mass adoption while keeping inflation resistance.
|
||||
- Our privacy is built on the mimblewimble protocol which is unique compared to other privacy protocols. Litecash transactions are not held on a ledger and disappear as opposed to other methods of scrambling or clustering which could actually be decoded with new wave super computers.
|
||||
- if a transfer does not complete due to a wrong address or defunct wallet, funds get sent back to the sender within 24 hours ensuring no lost coins.
|
||||
|
||||
_Observations_:
|
||||
- a fork can be misleading to non-techies mistaking it for a core protocol or misunderstanding as an original product
|
||||
- third party tech is proven within another community, original protocol engineers &/or researchers which could obscure search on audits, privacy validity
|
||||
- DeFi features aren't equal privacy features
|
||||
|
||||
_Product feature_
|
||||
- forkability x privacy 101
|
||||
- privacy tech vocabulary (mimblewimble, scrambling, clustering etc)
|
||||
|
||||
## **Black Box**
|
||||
|
||||
Answers:
|
||||
- For the transactions anonymizer, privacy is preserved when the onchain link between SENDER and RECEIVER wallets is broken or untraceable.
|
||||
_Observations:_
|
||||
- general privacy storytelling missing proof on untraceability (linkage between sender & receiver)
|
||||
|
||||
_Product feature:_
|
||||
- private transactions 101
|
||||
|
||||
## **Ergo**
|
||||
|
||||
Answers:
|
||||
- Ergo has the flexibility to implement privacy in various use cases. Although it is not a privacy-oriented blockchain, Sigma Protocols allow privacy-oriented dApps like ErgoMixer, or private side-chains, to obfuscate specific transactions https://t.co/KVNIk8amD1
|
||||
|
||||
_Observations:_
|
||||
- important to understand that protocols could be non-private, but activate private use-cases (partial implementation). Separate core tech from privacy narrative
|
||||
|
||||
_Product feature:_
|
||||
- case-studies (privacy matching): protocol = transparent, but use-cases = private (like Ethereum)
|
||||
|
||||
# Product summary
|
||||
|
||||
_Web3Privacy Now platform (for non-techies track) will consist of the multiple scoring model directions_:
|
||||
1. Validity track ("yes/no" applicability like if "docs" exist or not).
|
||||
2. 101 educational materials.
|
||||
3. Checklists (example: trusted sources list).
|
||||
4. Academy (content from case studies to third-party services to check net data, leakages).
|
||||
|
After Width: | Height: | Size: 115 KiB |
|
After Width: | Height: | Size: 163 KiB |
|
After Width: | Height: | Size: 107 KiB |
|
After Width: | Height: | Size: 70 KiB |
|
After Width: | Height: | Size: 188 KiB |
|
After Width: | Height: | Size: 61 KiB |
|
|
@ -0,0 +1 @@
|
|||
|
||||
|
After Width: | Height: | Size: 444 KiB |
|
After Width: | Height: | Size: 37 KiB |
|
After Width: | Height: | Size: 51 KiB |
|
After Width: | Height: | Size: 26 KiB |
|
After Width: | Height: | Size: 73 KiB |